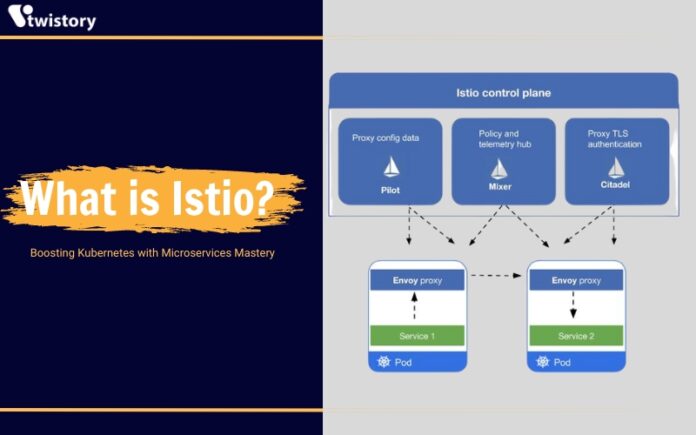
Introduced in 2017, Istio emerges as an essential service mesh that bolsters security, surveillance, and orchestration for applications encapsulated in containers. It embeds itself within the structural layers of cloud applications to seamlessly manage the underlying microservices infrastructure. In this Twistory article, we delve into what is Istio, unravel its functionality, and illuminate its primary benefits and considerations for deployment.
Istio is an open-source service mesh that offers a standardized method to connect, secure, manage, and monitor services. Operating as an infrastructure-agnostic overlay, Istio can be implemented atop various platforms like Kubernetes, Mesos, or any other underlying infrastructure.

The mechanism of Istio involves deploying a sidecar proxy alongside each service in the application. This proxy is responsible for intercepting all incoming and outgoing traffic, delivering a suite of functionalities such as:
- Service Discovery and Traffic Distribution: Istio automatically identifies services within the application and enables seamless inter-service communication. It also includes a load-balancing feature that evenly spreads traffic among multiple service instances.
- Secure Communications: Through TLS encryption, Istio ensures that all service-to-service communication is secure, safeguarding data from eavesdropping or tampering.
- User and Service Authentication/Authorization: Istio provides mechanisms for verifying user and service identities and can enforce access policies, thereby restricting application access to verified users and services.
- Traffic Management: With Istio, you gain granular control over traffic routing, enabling the implementation of sophisticated patterns for traffic flow, such as A/B testing or phased rollouts with canary deployments.
- Fault Injection: To enhance the robustness of applications, Istio can introduce controlled faults, including delays and failures, enabling developers to test how well the application withstands various fault conditions.
- Observability: Istio collects comprehensive metrics and telemetry data, providing insights into the application’s operational metrics, which can be critical for performance tuning and identifying health issues.
What is Istio?
What does Istio mean for Kubernetes users?
Istio serves as a service mesh optimized for Kubernetes, streamlining the networking, security, and monitoring complexities associated with cloud-native applications. It offers a cohesive control plane that oversees microservices sprawled across diverse Kubernetes clusters. With Istio, you can enforce numerous capabilities and patterns, including service detection, efficient load distribution, robust security protocols, precise traffic direction, and comprehensive metrics gathering.
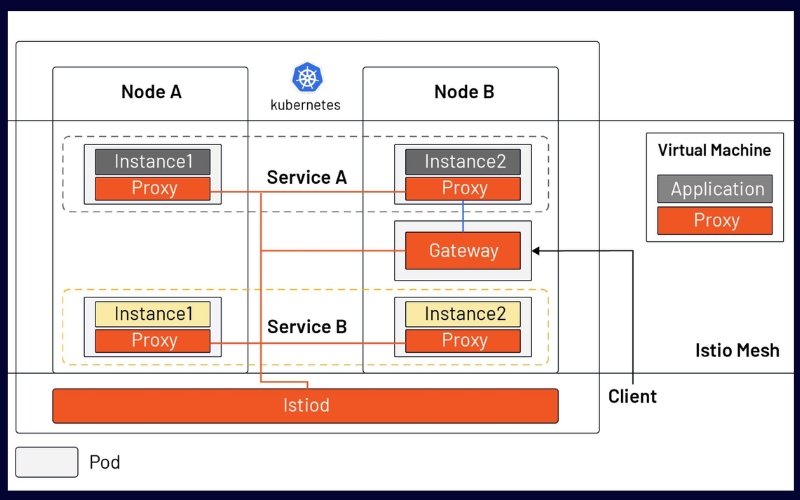
This mesh empowers developers and operators with tools for more efficient construction and maintenance of cloud-native applications by offering a unified management interface, fortified security, boosted system dependability, and expanded visibility into system performance and behavior.
Understanding the Working of Istio
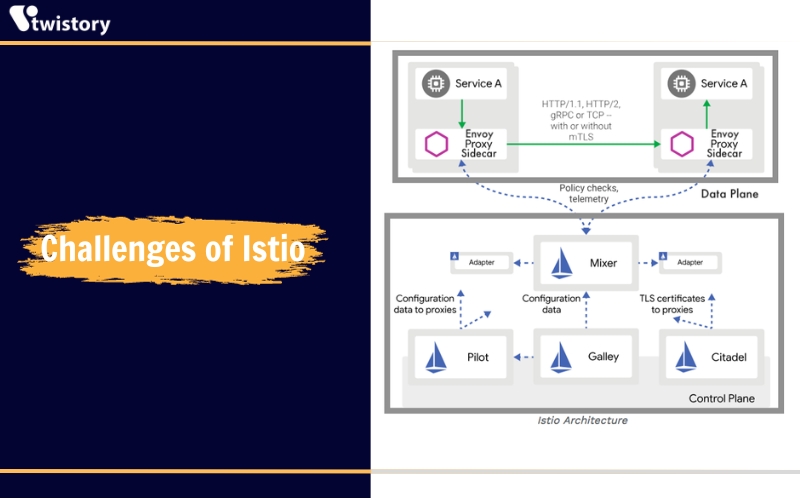
The architecture of Istio is fundamentally composed of two primary elements: the control plane and the data plane. Central to the data plane is Envoy, an open-source service proxy that abstracts networking complexities away from the underlying applications. This proxy is configured with a set of network filters which can be customized to manage incoming and outgoing traffic. Moreover, for handling HTTP traffic, Envoy provides the added functionality of an L7 layer filter. Let’s delve deeper into the intricacies of both the data plane and the control plane components:
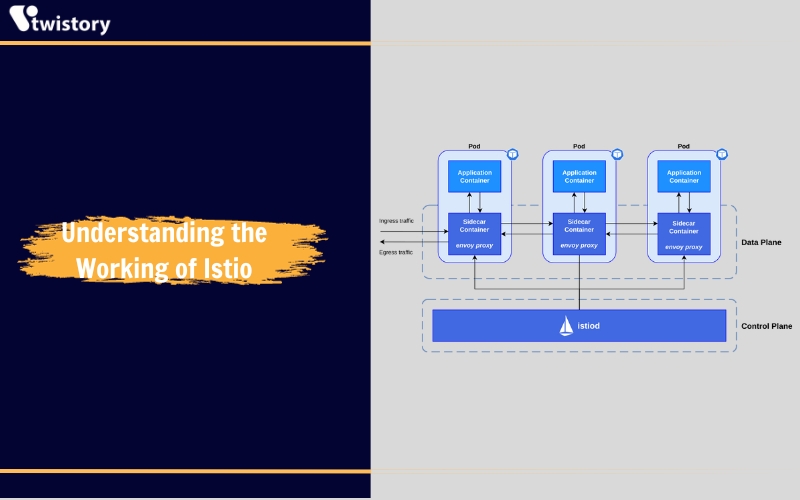
The data plane
In the data plane, services are augmented by embedding a sidecar proxy into the environment. This proxy is paired with a microservice and facilitates the handling of incoming and outgoing requests among other proxies. These proxies collectively form a mesh network that regulates direct network communication between microservices.
Absent this plane, service intercommunication would falter, and the network would lack the ability to discern and appropriately route various types of traffic based on origin and destination. Istio’s service mesh enables a suite of application-aware capabilities that are leveraged based on the system’s configuration. The capabilities of the Envoy proxies integral to Istio’s service mesh offer a multitude of functionalities, which include:
- Traffic Control: Envoy provides sophisticated mechanisms to manage application traffic, including support for gRPC, HTTP, WebSocket, and TCP routing. This is pivotal for optimizing performance and crafting advanced deployment methodologies. Istio’s traffic management API permits granular traffic control within the service mesh, expanding the types of manageable traffic.
- Routing and Rules: Key API resources for traffic direction within Istio are virtual services and destination rules. Virtual services define the mesh’s routing behavior for service requests through an ordered set of rules. Concurrently, destination rules establish policies to route traffic to its intended endpoint.
- Network Robustness: Istio inherently supports features like automatic retries, fault injections, and circuit breaking to bolster network resiliency.
- Enhanced Security: Istio commences security measures by assigning verifiable identities to each service. In tandem with its agents, which work alongside every Envoy proxy, Istio automates the management of key and certificate pair rotation. For various scenarios, it offers peer and request authentication options. Peer authentication, often used in conjunction with Istio’s full-stack mutual TLS solution, is preferred for service-to-service authentication, whereas JSON Web Token validation can be executed through Istio using either a custom or OpenID Connect (OIDC) provider.
- Access Control and Compliance: Envoy is capable of executing access controls, imposing rate limits, and enforcing security policies on inter-service communications.
- Encryption and AAA Protocols: Istio facilitates transparent TLS encryption and authentication, fortified identity assurance, and comprehensive policy, audit, and authorization tools to secure data and services across even untrusted networks, embodying a security-by-default posture and providing layered defense mechanisms for the secure deployment of applications.
The control plane
The control plane takes the desired configuration and its own view of the services and actively reprograms the proxy servers in response to changes in the environment or policies. It is tasked with the setup and administration of the proxies to facilitate traffic routing. The core functionalities of the control plane encompass:
- Ensuring secure service-to-service communication within the cluster by implementing transport layer security (TLS) encryption, authorization, and robust identity verification.
Providing capabilities for detailed and nuanced traffic management through failovers, retries, sophisticated routing directives, and fault injections. - Facilitating automatic load distribution for traffic types like HTTP, WebSocket, gRPC, and TCP.
- Systematically gathering and processing metrics, telemetry, and logs for all traffic within a cluster.
- Implementing access controls, rate limits, and quotas using a configuration API coupled with a modular policy framework.
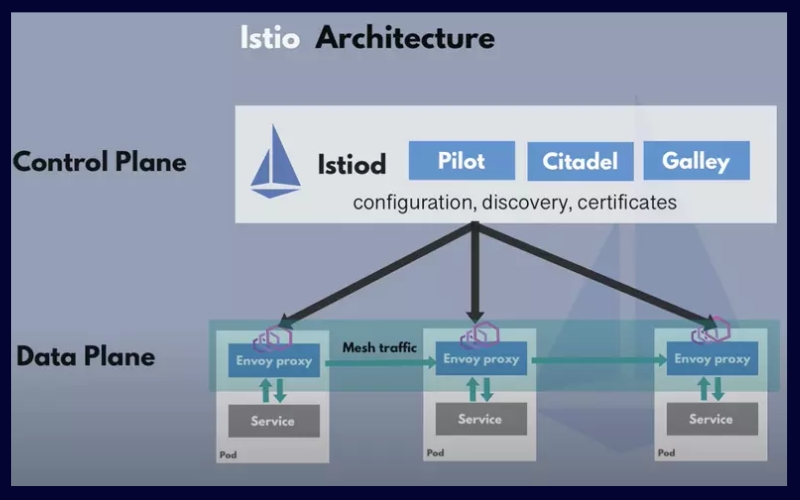
Architectural diagram of Istio
The architectural schematic of Istio delineates the components comprising both the control and data planes. It illustrates services A and B, each interfaced with proxies, through which data is channeled, forming a mesh network of traffic flow.
11 3 Istio 1 5 Architecture
Top 10 Benefits Of Istio
When integrated, Istio and Kubernetes provide a seamless operational experience for a containerized microservices-based system. Istio is platform-agnostic and capable of functioning across various environments, such as cloud infrastructures, on-premises setups, Kubernetes clusters, or Mesos. With Istio, DevOps practitioners can gain insights into the interactions of monitored services, bolstered by its comprehensive telemetry which encompasses distributed tracing, granular metrics, and complete access logs. Collectively, these features offer a multitude of benefits.
A higher degree of observability
Istio within a Kubernetes environment enables precise observability and in-depth understanding of the observed distributed services. It aids in acquiring detailed knowledge of the interactions occurring at the application layer. Offering control and insight over both traditional and modern workloads, including containers and virtual machines, it delivers a transparent layer of communication for applications running discretely within the cluster.
An increased emphasis on safety
Istio achieves this through the provision of mutual Transport Layer Security (mTLS), acting as an all-encompassing mechanism to apply security and compliance protocols, verify service identities, and encrypt inter-service traffic, thus enhancing the security of exchanges within the communication network. Moreover, it focuses on fortifying the application-level security infrastructure by employing strong identity-based multi-factor authentication, authorization, and encryption methods.
Efficient management of the flow of traffic
Istio enhances the governance of traffic within services through detailed routing directives, backup paths, retry logic, and deliberate fault introduction. In the phase of post-production testing, leveraging Chaos Monkey in conjunction with Istio allows site reliability engineers to deliberately inject disruptions such as time delays and errors, thereby increasing the system’s durability. The traffic management aspect of Istio plays a crucial role in separating the patterns of traffic from the expansion capabilities of the underlying infrastructure.
Seamless traffic routing
Istio plays a crucial role in orchestrating network traffic control, determining the destination of incoming service requests. It directs the stream of traffic and the invocation of APIs among distributed services, enabling smart routing capabilities. Requests, upon being mapped to the correctly configured API endpoints, are deemed API calls. After the configuration phase is finalized, all data is transmitted and processed, culminating in the delivery of the response.
Increased overall productivity of developers
For an effective application deployment, developers should primarily focus on writing code. Additionally, they are often tasked with building libraries to handle inter-service communication across various programming languages. Employing Istio can help overcome these complexities. It empowers developers to direct their attention solely to the application’s business logic, while supplying the essential functionalities for supporting microservices. This shift allows developers to dedicate more of their efforts and resources to the core facets of software creation.
Simplified service monitoring
Istio provides visibility at the service level, which supports tracing and monitoring, thereby aiding in the resolution of issues. Lacking detailed data about a problem can make it difficult to identify and rectify performance bottlenecks. Utilizing a service mesh such as Istio allows for the rapid isolation of malfunctioning services, enabling the deactivation of inoperative instances while preserving the responsiveness of the API.
Strong support for multi-cloud
Istio within Kubernetes is platform-agnostic, meaning users who integrate Istio with Kubernetes can navigate container-based architectures, allowing for systems to be architected to function across diverse cloud environments. It serves as a robust tool for enhancing security in service-to-service interactions, diagnosing issues, and managing traffic flow, whether the deployment is in a public cloud, on-premises data center, or a hybrid cloud setup.
Simplified load balancing and policy management
Within a Kubernetes environment, Istio facilitates automatic load balancing across traffic types, along with advanced features such as client-side routing, as well as blue-green and canary deployment strategies. Additionally, Istio manages policy enforcement through a configurable API and a modular policy framework that provides support for access control measures, rate limiting, and quota management. The policies enforced can be tailored and are seamlessly integrated with ACLs, along with logging and monitoring systems.
Enhanced microservice and infrastructure functionality
Istio facilitates the management of microservices across their growth spectrum and provides traffic management capabilities among them. It segregates the proxy layer that ensures the accurate routing of requests between services. Enhancing both the performance and reliability of the infrastructure, Istio gathers telemetry data from proxy containers and relays it to a monitoring interface. Moreover, Istio is equipped to withstand uncertain network disruptions and supports the self-recovery of the infrastructure.
Improved infrastructure scalability
Within a Kubernetes setup, Istio can support organizations running extensive applications composed of numerous microservices. With escalating application traffic, the surge in service-to-service requests demands sophisticated routing techniques to streamline data traffic and maintain the application’s optimal performance. Istio’s service mesh empowers developers to enhance each newly developed service instead of concentrating on the connectivity between services.
For DevOps teams that have established CI/CD processes in production, a service mesh becomes essential to programmatically roll out applications and their infrastructure. It integrates with version control and automated testing tools such as Jenkins, Git, Artifactory, and Selenium to facilitate the management of network and security configurations through code.
Challenges of Istio
While a service mesh like Istio aims to address many issues inherent in microservice architectures, it’s not without its drawbacks, which include:
- Increased complexity: Introducing proxies and other components adds an extra layer of infrastructure, complicating both development and management.
- Expertise gap: Incorporating a service mesh alongside orchestrators such as Kubernetes requires operational teams to master both, demanding significant technical knowledge and training.
- Performance impact: The invasiveness and complexity of service meshes like Istio can lead to reduced system performance due to the overhead of additional proxies that must be navigated with each service call.
- Documentation deficiencies: Adapting to Istio’s intricacies requires access to up-to-date and comprehensive documentation, which is often lacking, leaving gaps in how certain tasks should be performed.
- Configuration demands: Although Istio can be deployed with default settings in Kubernetes environments, advanced setups, like those required for chaos engineering, demand more intricate configurations that can be time-consuming without expert intervention.
- Coverage constraints: Despite its strengths in enhancing resilience and deployment management, Istio’s diagnostic and telemetry features are limited to the services within its scope, lacking a holistic view of every service a transaction may interact with outside the Kubernetes environment.
- Visibility risks: Achieving thorough distributed tracing with Istio may necessitate manual code adjustments for each service, which still might not provide complete insight into the services’ inner workings. Without significant investment in custom logging tools, visibility across a Kubernetes cluster could be inadequate.
In unraveling the layers of microservices management, we’ve journeyed through the essence of “what is Istio“ and how it interlinks with Kubernetes to orchestrate a streamlined, secure, and observable service mesh. The versatility and robustness of Istio not only pave the way for efficient traffic management but also fortify the security and observability across the service interactions. The challenges, albeit present, are overshadowed by the immense capabilities and benefits that Istio brings to the table. As we’ve explored, the blend of Istio and Kubernetes potentially holds the key to transforming the complex maze of microservices into a navigable, well-managed ecosystem.
The realm of Istio is vast and filled with possibilities waiting to be explored. If this piqued your interest, we invite you to delve deeper into the sea of knowledge by exploring more blogs at Twistory. The expedition into Istio’s universe doesn’t end here; it’s just the beginning of a continuous learning voyage. So, continue sailing on the waves of discovery with Twistory and enrich your understanding of the technologies that are shaping the modern microservices landscape.