Tired of hitting digital walls while trying to access your favorite websites? Ever wondered how to bypass Cyberoam’s restrictions that seem almost like a virtual guard blocking your online freedom? Whether you’re at school, work, or any institution that uses Cyberoam for network security, we’ve got some tech tricks up our sleeves just for you.
In this blog, we’ll walk you through multiple ways how to bypass Cyberoam without login and unlock a world of unrestricted internet access. Trust us, you’ll want to stick around for this enlightening digital journey.
Note: Cyberoam network security continually receives updates and evolves its network management methods. Therefore, the techniques for bypassing Cyberoam network security that may have been valid when you’re reading this article could no longer be effective. Nevertheless, it’s worth attempting to bypass it.
Is Cyberoam A Firewall?
Cyberoam presents a comprehensive firewall platform tailored for enterprises, irrespective of their scale. It boasts progressive capabilities like application management, content screening, and user-specific protocols, ensuring a fortified and confidential network environment.
With its real-time threat detection and defenses against spam and malware, Cyberoam stands as a preferred firewall choice for businesses aiming to safeguard their networks and data from potential harm.
Is It Actually Possible To Avoid Cyberoam?
Proxies and technological configurations can sometimes be intricate. Many services, when set up correctly, tend to be restrictive to ensure security. However, a little-known fact is that even with stringent measures, certain loopholes can be found.
These gaps allow savvy users to navigate around restrictions, offering ways to hack Cyberoam. Overcoming these limitations can be particularly beneficial if you’re trying to access specific online information, but the source is among the filtered sites.
How To Bypass Cyberoam
Navigating the maze of internet restrictions can be a hassle, especially if you’re working or studying in an environment that uses Cyberoam for network security. However, like any system, it’s not entirely foolproof. Here are some savvy tactics you can employ to bypass Cyberoam login and work around these limitations.
Using Tor Browser
For unrestricted browsing, consider using the Tor Browser. Based on Mozilla Firefox but supercharged for privacy, Tor helps you become virtually invisible online.
The browser routes your connection through the Tor network, masking your location and making it almost impossible for anyone to trace your activities. Utilizing the Tor IP address, it can even navigate around specific limitations posed by Cyberoam network security.
IP Address Translation
Typically, it’s the website’s URL that’s blocked, not its IP address. However, keep in mind that a website’s IP can change over time, so blocking it might not always be effective. To access a website using its IP address, input the IP directly into the browser’s address bar.
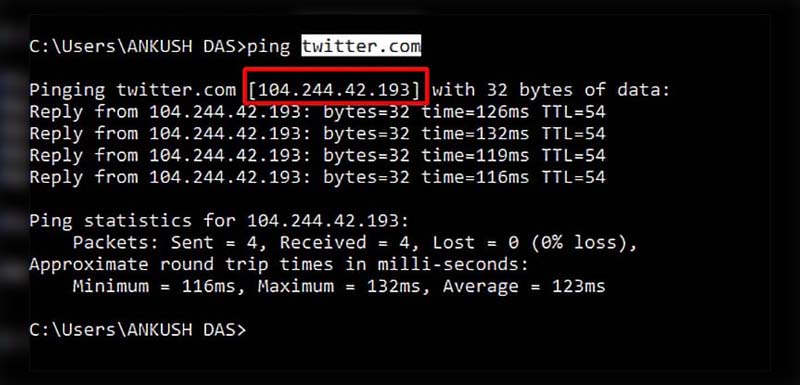
- To determine a site’s IP address, you can either: Use the command prompt on Windows. Simply open the command prompt and enter:
- Type the command:
ping anywebsitename.com(replace .com with the website’s actual domain, and adjust the extension as needed).
The resulting output will show the website’s IP address.
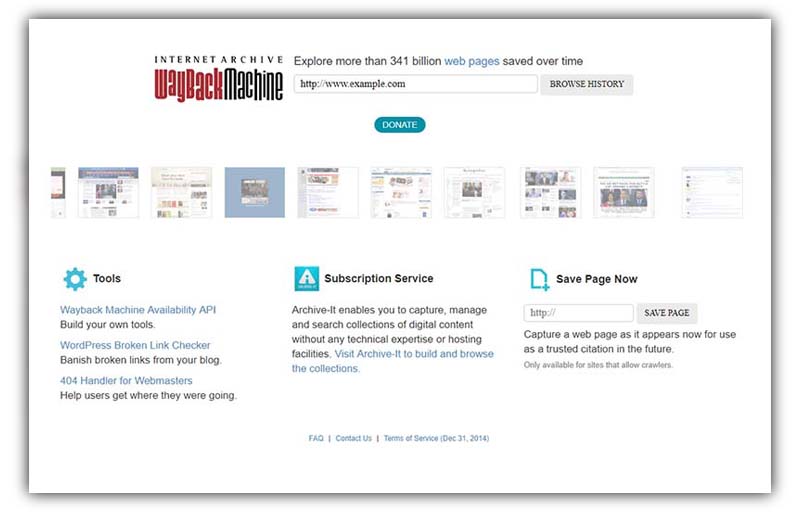
Access Archived Web pages
For those keen on accessing stable content from websites that remain largely unchanged over time, there’s a handy solution. Consider exploring archived versions of the website through online archival services.
WayBackMachine
One of the premier tools for this purpose is the Wayback Machine. This remarkable service archives “snapshots” of web pages, preserving them for future reference.
However, it’s essential to understand that not every page from a website is archived daily. So, while delving into its vast database, you might need to do a bit of searching to locate the specific content you’re after.
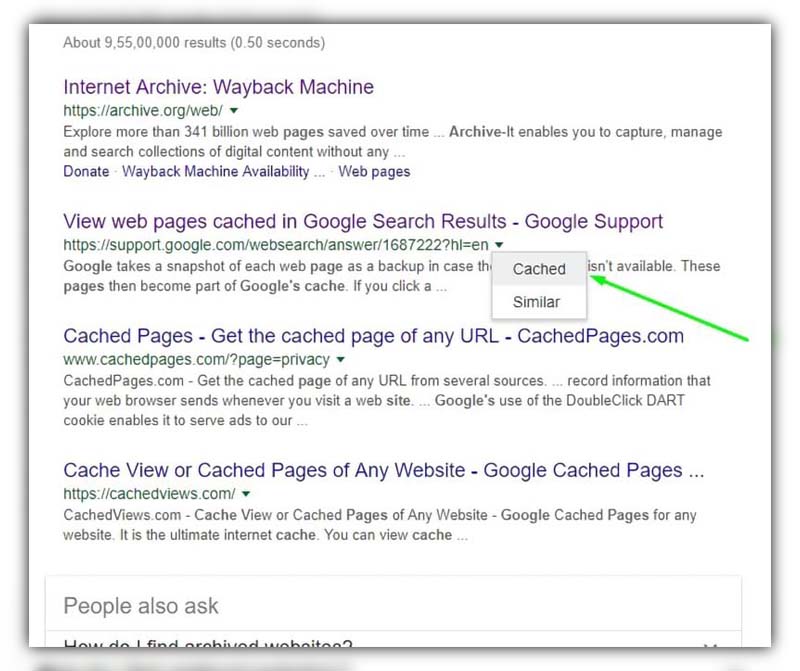
Google Cached Page
Another neat trick is using Google’s cached pages. Simply perform a Google search for the site you want, click the little green arrow next to the URL, and select ‘Cached.’ This often works, but not every page will have a cached version available.
Use A VPN
Utilizing a VPN, which stands for Virtual Private Network, is the prime strategy to sidestep Cyberoam’s restrictions. VPNs excel at navigating internet roadblocks and censorships.
Beyond that, they offer the added advantage of online anonymity, ensuring your browsing activities and app usage remain private and undetectable.
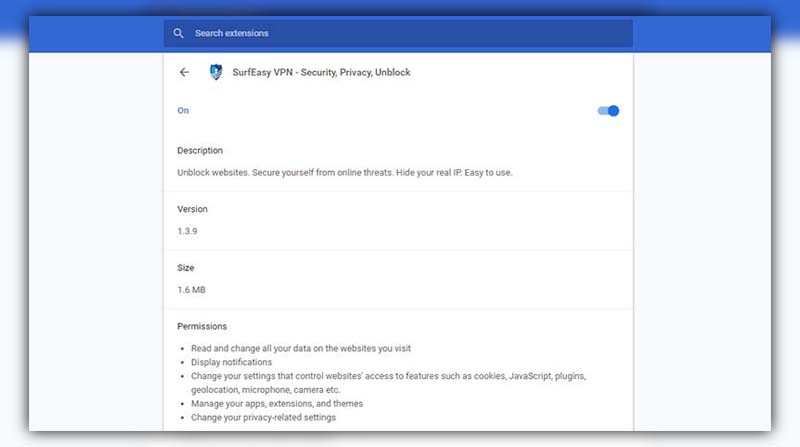
Use Google Chrome Extensions
Extensions like SurfEasy or Zenmate can be your quick fix. These mini-programs attach to your Google Chrome browser and act like a mini-VPN, offering you a bypass Cyberoam proxy server route for website restrictions.
Secure URL
In certain instances, websites that typically use the HTTP protocol might also support HTTPS, especially if they have an SSL certificate in place.
For instance, if you’re trying to access “http://techreviewpro.com“, consider switching to “https://techreviewpro.com“.
Using HTTPS ensures an encrypted connection, enhancing security. However, it’s worth noting that while the connection is encrypted, the website can still track your visit.
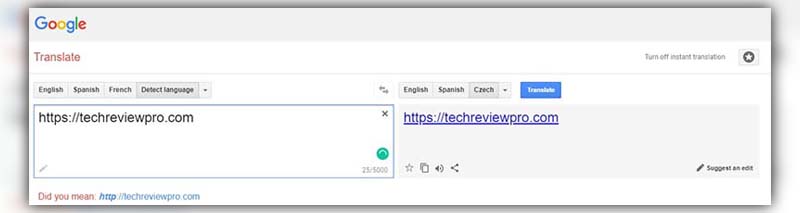
Utilize Google Translate
A straightforward yet effective trick to bypass website restrictions without resorting to VPNs or proxies is leveraging Google Translate. Here’s how:
- Step 1: Navigate to Google Translate’s main page.
- Step 2: Enter the URL of the restricted website you’d like to access.
- Step 3: Choose a language for translation. The specific language isn’t crucial; just pick one you’re comfortable with, as the interface suggests.
- Step 4: Once you’ve made your selection, hit “
Translate“ - Step 5: The website should now be accessible, unrestricted.
However, a word of caution: If Google Translate itself is restricted, give both the local domain version (like the Indian domain for users in India) and the global version a try to see if you can access either.
Ethical Considerations When Bypassing Cyberoam
Navigating around Cyberoam is feasible, but it’s paramount to approach this with responsibility and ethics in mind. Always adhere to your network administrator’s guidelines.
While browsing, exercise caution about the websites you access and the links you click, especially if they redirect you to potentially unsecured sites.
Platforms like YouTube, Netflix, and Spotify are generally safe due to their reputable content. However, social media, with its myriad of third-party links, demands extra caution. Especially in sensitive environments like schools or workplaces, it’s prudent to be wary of external links that might jeopardize the network’s integrity.
Access Blocked sites, bypass Cyberoam, hack Cyberoam
For those on Android or iOS, a quick search in the app store will yield numerous free VPN options. However, it’s crucial to research and verify any app before downloading, particularly on Android, given the occasional presence of counterfeit applications. Always scrutinize app permissions and be wary of what data they may access or store.
Using a VPN or browser extension like those for Chrome or Firefox has become an increasingly popular way to navigate around Cyberoam restrictions. With a plethora of tools available, bypassing Cyberoam has become more accessible than ever.
How To Bypass Cyberoam On Android Phone At My College
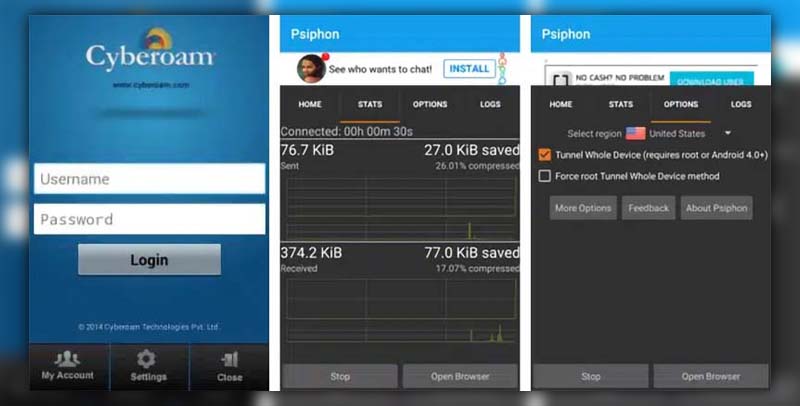
On your Android device, follow these steps to bypass Cyberoam using Psiphon:
- Step 1: Launch the Google Play Store and search for Psiphon. Proceed to install it.
- Step 2: Once installed, open Psiphon. A prompt will ask for permission to set up the VPN connection on your device. Simply hit ‘OK’.
- Step 3: Click on the ‘Start’ button to activate Psiphon.
- Step 4: You should now be able to access Wi-Fi without encountering a login page.
Note: Psiphon functions as a straightforward VPN service. It lets you select a region for a secure connection, enabling you to circumvent Cyberoam on your Android device in a matter of seconds.
In summary, bypass Cyberoam doesn’t have to be a complicated tech maze. We’ve unpacked multiple ways for you to maneuver around network restrictions and reclaim your online freedom. Now, the digital world is quite literally at your fingertips.
If you found this guide useful, we’ve got plenty more tech-savvy insights and how-to guides over at Twistory. Don’t let any more digital barriers hold you back – check out our other blogs and continue to explore your online world, unrestricted.