Are you noticing unexpected changes in your browser settings? Experiencing frequent pop-ups or redirects? Your system might be under the threat of the “Chromium Virus”. This blog post is a must-read for you. It provides an in-depth understanding of the Chromium Virus, its potential risks, and effective strategies to safeguard your system.
Definition and Purpose of Chromium
Chromium is a web browser project that is not only free but also open-source. It is primarily developed and maintained by Google with the objective of providing a safer, faster, and more stable web experience for all users. The open-source codebase of Chromium serves as the backbone for many renowned web browsers, including Google Chrome.

Here are some pivotal aspects of Chromium’s mission:
- Accessibility and transparency: The open-source nature of Chromium allows anyone to examine, alter, and contribute to the code. This fosters transparency and cooperation in the development of the browser.
- Platform independence: Chromium boasts the ability to operate on a variety of operating systems, including Windows, macOS, Linux, Android, and more.
- Customization and innovation: The open-source characteristic of Chromium empowers developers to fabricate custom versions of the browser, complete with additional features or modifications.
- Security focus: Chromium places a high priority on security, implementing features such as sandboxing, regular updates, and mechanisms for detecting vulnerabilities.
Differences between Chromium and Google Chrome
| Feature | Chromium | Google Chrome |
| Open-source | Yes | No (uses Chromium’s codebase, but adds proprietary features) |
| Code availability | Publicly accessible | Controlled by Google |
| Customization | Highly customizable | Limited customization options |
| Updates | Manual or through third-party repositories | Automatic updates from Google |
| Features | Basic web browsing functionalities | Additional features like auto-fill, bookmark syncing, video conferencing plugins, Google services integration |
| Media codecs | Lack of built-in support for some codecs (e.g., MP3, H.264) | Includes built-in codecs for most popular formats |
| Brand | No built-in branding | Features Google branding and integrations |
| Privacy | No built-in user tracking | May collect and use browsing data for targeted advertising and personalization |
| Security | Regular security updates, but manual installation | Automatic security updates from Google |
| Target audience | Developers, power users | General users |
Understanding the Chromium Virus
It’s crucial to note that Chromium, in its essence, is not a virus but a legitimate open-source project. However, the term “Chromium” can be exploited by developers of malevolent web browsers to feign legitimacy and mislead users. These detrimental browsers are commonly dubbed as the “Chromium virus.”
Definition of Chromium Virus
The term “Chromium virus” is used to describe misleading and potentially damaging web browsers that are constructed using the authentic Chromium codebase. Their objective is to deceive users into downloading and installing them, with the intent to pilfer data, introduce malware, or interfere with browsing activities.
How the Chromium Virus Operates
These malevolent browsers utilize a variety of strategies to proliferate and function:
- Impersonating legitimate software: They may adopt names strikingly similar to well-known browsers such as Chrome, Edge, or Firefox, often appending “new” or “pro” to give an impression of being updated.
- Bundling with freeware or pirated software: They can be concealed within the installation files of seemingly innocuous programs, thereby infecting your system concurrently.
- Phishing attacks: Deceptive alerts or download prompts masquerading as security warnings or software updates can dupe users into installing the virus.
Upon installation, the Chromium virus can:
- Usurp your default browser: It can supplant your chosen browser with its own variant, making it challenging to revert.
- Alter your homepage and search engine: It can redirect you to malicious websites or search engines that infuse ads or monitor your activity.
- Monitor your browsing data: It can pilfer your browsing history, passwords, and other confidential information.
- Install supplementary malware: It can download and introduce other harmful programs onto your system to inflict additional damage.
Signs of Chromium Virus Infection
Stay alert for these signs that may suggest your system is compromised:
- Unanticipated browser modification: Your default browser undergoes changes without your awareness or approval.
- Unrecognized homepage and search engine: Upon launching your browser, you find yourself on unfamiliar websites or utilizing a different search engine.
- Pop-up advertisements and redirections: You encounter an escalated number of undesired pop-up ads or are frequently redirected to dubious websites.
- System deceleration and crashes: Your computer exhibits recurrent slowdowns, crashes, or instability.
- Unknown browser operations: Unfamiliar background processes associated with unknown browsers materialize in your task manager.
Risks of the Chromium Virus
The Chromium virus presents several substantial threats to your system and online security. Let’s delve into the specific risks in greater detail:

Impact on Privacy and Data Security
- Data pilferage and breaches: The virus has the capability to track and purloin sensitive data such as browsing history, login credentials, credit card information, and even personal documents, thereby exposing you to risks of identity theft, financial losses, and online harassment.
- Invasion of privacy: By scrutinizing your browsing activity and online interactions, the virus can construct a comprehensive profile of your interests, habits, and preferences, which can be exploited for targeted advertising, scams, and other malevolent purposes.
- Tracking and surveillance: The virus can be employed to trace your online movements and activities across diverse websites and platforms, potentially even overseeing your location and device usage.
Effects on Computer Performance
- Resource monopolization: The virus can guzzle excessive CPU, memory, and network bandwidth, significantly decelerating your computer. This can render basic tasks like browsing, document editing, and application execution frustrating and inefficient.
- System instability: The virus can instigate conflicts and errors within your system, leading to recurrent crashes, freezes, and unexpected shutdowns. This can disrupt your workflow and potentially jeopardize your data.
- Battery depletion: The escalated resource consumption can drain your laptop battery faster, curtailing its portability and usability.
Risks Associated with Other Malware
- Gateway for additional threats: The Chromium virus can serve as a conduit for downloading and installing other malware onto your system, including ransomware, Trojans, and spyware. These additional threats can inflict even more damage to your computer and data.
- Financial losses: Malware can be utilized to steal your financial data, such as credit card details or bank account numbers, leading to financial losses and identity theft.
- Personal harm: Certain types of malware, like ransomware, can lock you out of your own files or encrypt your data, demanding ransom payments to regain access. This can be incredibly disruptive and cause significant personal distress.
Prevention and Remediation Measures
Protecting yourself from the Chromium virus and other online threats requires a proactive approach. Here’s a comprehensive guide to prevention and remediation measures:
How to Avoid Installing the Chromium Virus
Exercise prudence with downloads:
- Download software exclusively from trusted sources: Adhere to official app stores, developer websites, and credible software repositories. Steer clear of third-party download sites or dubious links in emails.
- Be attentive during installation: Scrutinize the installation prompts meticulously and decline any supplementary downloads or bundled software.
- Regularly update your software: Consistently update your operating system, web browser, and other software to rectify vulnerabilities that malware could exploit.
- Utilize a web browser equipped with inherent security features: Browsers such as Chrome, Firefox, and Edge all possess built-in defenses against malware and phishing.
- Be skeptical of unexpected browser pop-ups and alerts: Authentic software seldom employs pop-ups to prompt updates or downloads. Close them judiciously and refrain from clicking on suspicious links.
- Scan downloaded files prior to opening them: Employ a reputable antivirus program to scan downloaded files before opening them.
Detailed Guide to Removing the Chromium Virus
Identification of the Chromium Virus:
- Inspect your installed programs: Search for unfamiliar programs named “Chromium”, “Chrome Plus”, “Web Companion”, etc.
- Validate browser settings: Examine your homepage, search engine, and default extensions for unauthorized alterations.
- Observe browser behavior: Look out for unusual pop-ups, redirects, or sluggish performance.
Steps for Removal:
- Deactivate suspicious extensions: Access your browser’s extension settings and disable any that you don’t recognize or haven’t installed yourself.
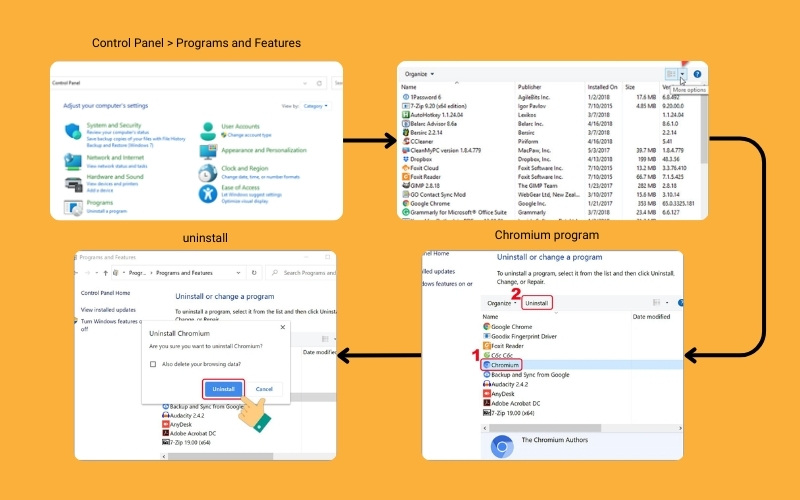
- Uninstall the Chromium Virus:
Windows: Navigate to Control Panel > Programs and Features, locate the Chromium program, and uninstall it.
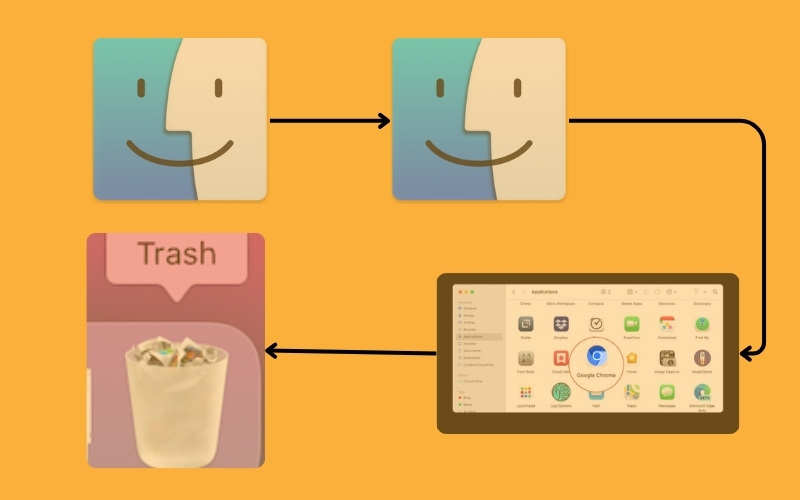
Mac: Proceed to Finder > Applications, drag the Chromium app to the Trash, and empty the Trash.
- Reset browser settings: Most browsers come with a built-in option to reset settings to default. This will eliminate any unwanted changes instigated by the virus.
- Execute a full system scan: Utilize your antivirus software to conduct a comprehensive scan of your entire system to detect and eradicate any residual malware.
- Contemplate additional cleaning tools: Specialized anti-malware programs like Malwarebytes or AdwCleaner can assist in removing stubborn remnants of the virus.
Antivirus Software and Other Useful Tools
Antivirus Software:
- Norton AntiVirus: Renowned for its all-encompassing protection and sophisticated features.
- Bitdefender Antivirus Plus: Exceptional at detecting and preventing malware, with minimal impact on system performance.
- McAfee Antivirus Plus: Provides robust protection with features such as identity theft protection and parental controls.
- Kaspersky Total Security: Delivers comprehensive security with antivirus, anti-spam, firewall, and anti-ransomware protection.
Other Beneficial Tools:
- Malwarebytes Anti-Malware: Effectively removes malware and adware that traditional antivirus software may not detect.
- AdwCleaner: Conducts scans and eliminates unwanted adware and browser extensions.
- Junkware Removal Tool: Purges your system of superfluous software and bloatware.
Conclusion
In conclusion, the Chromium Virus is a significant threat that can compromise your system and data. This blog post has provided you with a comprehensive understanding of this virus, its potential risks, and effective strategies to safeguard your system. Remember, knowledge is the first line of defense. For more insightful content on similar topics, don’t forget to explore other blogs on Twistory.net. Stay informed, stay secure


