Are you concerned about your online privacy? Do you feel your internet activities are being watched? If so, you’re not alone. This blog post is a must-read for you. We’ll delve into the concept of “Onion Over VPN”, a technology that takes your online anonymity to the next level. Stay tuned to learn how it works and why you might need it in your digital life.
Understanding the Operation of Onion Over VPN
While both Tor and VPN are designed to enhance your online privacy and security, they operate in fundamentally different ways. Tor aims to provide total anonymity, while a VPN is designed to ensure privacy.

These two tools can be used together to further bolster your online privacy and security. This is achieved by connecting to a VPN server before accessing the Tor network, a method known as Onion over VPN.
Here’s a simplified explanation of how Onion over VPN works:
- When you connect to a VPN server, it establishes an encrypted tunnel between your device and the VPN server. This hides your browsing activity and IP address from your Internet Service Provider (ISP) and other potential eavesdroppers.
- If you then access the Tor network while connected to the VPN, the first node in the Tor network (known as the guard node) will only see the IP address of your VPN server, not your actual IP address. This provides an extra layer of privacy.
- Your web traffic is decrypted once it leaves the VPN server, but it still carries the IP address of the VPN server.
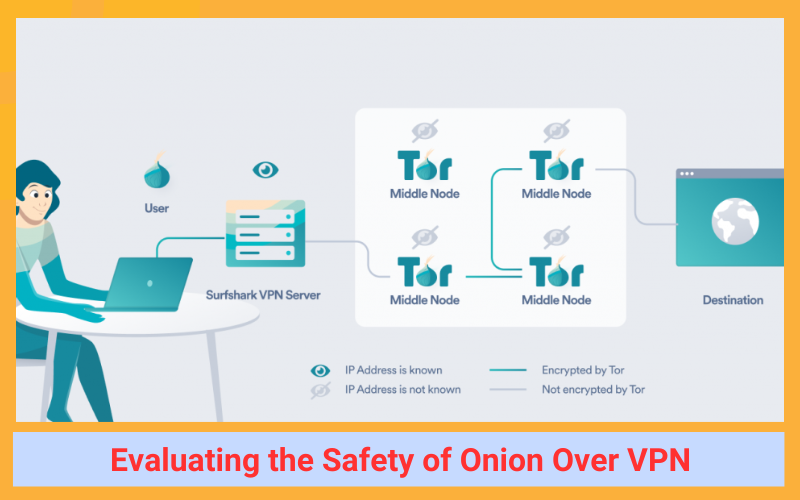
- As your traffic moves through the Tor network, it passes through three nodes (the guard node, a middle node, and an exit node), each of which adds an additional layer of Tor encryption. At each node, one layer of encryption is removed.
- At the exit node, your traffic is decrypted before it reaches its final destination. The exit node can see your browsing data, but it doesn’t know the IP address of your VPN server.
In essence, the VPN server acts as an additional node in the data transfer process. This means that when using Onion over VPN, your traffic is protected by four layers of encryption, compared to three layers when using Tor alone.
Evaluating the Safety of Onion Over VPN
Using a VPN in conjunction with the Tor network offers an added layer of privacy and security, enhancing your safety on Tor. However, it’s not a foolproof solution.
Onion over VPN serves to safeguard your traffic and shield your browsing habits from prying eyes. It keeps your ISP in the dark about your use of Tor and prevents your VPN service from tracking your activities.
Despite these advantages, Onion over VPN is significantly slower and less convenient than using the Tor browser alone. Therefore, it’s recommended only in extreme situations where security is of utmost importance.
Below is a comparison of the advantages and disadvantages of Onion over VPN to help you decide if it’s the right choice for you:
| Advantages | Disadvantages |
| Adds an extra layer of encryption | Cannot dictate the location of your IP address |
| Allows access to the Tor network in locations with geographical restrictions | Connection speeds are significantly slower |
| Your ISP won’t know you’re using Tor | Websites frequently block exit nodes |
| Your VPN service can’t monitor your browsing activity | Your VPN service will be aware you’re using Tor, but won’t know what you’re doing |
| The Tor guard node won’t see your IP address | Your VPN service will know your IP address |
| Offers protection against certain types of malware | Tor only supports the TCP protocol |
| Safeguards against complete de-anonymization in traffic correlation attacks |
Limitations on Monitoring by Your ISP and VPN
The use of Tor is often linked to illicit activities due to its connection with the dark web, which can potentially flag you for government surveillance.
Employing Onion over VPN can mitigate this risk as your Internet Service Provider (ISP) will be unaware of your Tor usage.
While your VPN service will be aware of your connection to Tor, it won’t have visibility into your activities within the network. Even if your VPN service maintains connection logs, it won’t be able to determine the specific websites you visit within the Onion network.
Moreover, the Tor guard node will only see the IP address of your VPN server, not your actual IP address, offering an extra layer of privacy.
Risks from Malicious Exit Nodes
A VPN provides encryption for all internet traffic between your device and the VPN server. When you use Onion over VPN, your traffic is decrypted after it leaves the VPN server and is then sent to the Onion network.
Within the Onion network, your traffic undergoes three additional rounds of encryption and decryption before it reaches its final destination. The traffic is finally decrypted at the exit node, which allows third parties to see your online activity, but not your identity.
Tor is a community-driven network where anyone can set up nodes, potentially enabling them to monitor your activity. An exit node that is configured to spy on or exploit Tor users is referred to as a malicious exit node.
If you access web servers using HTTP while using Onion over VPN, your traffic is not encrypted between the exit node and the web server, making it visible to malicious exit nodes.
On the other hand, if you access web servers using HTTPS while using Onion over VPN, your traffic remains encrypted between the exit node and the web server. This means that while exit nodes can see the data packets being transmitted, they cannot decrypt them.
Protection Against Malware
Tor is sometimes vulnerable to malware attacks. However, when you use Onion over VPN, your VPN can serve as a shield between your device and potential ransomware by protecting open ports via the VPN server’s firewall.
Open ports are responsible for receiving and transmitting TCP and UDP communications. While they are generally not harmful, they can be exploited to distribute malware and gain unauthorized access to personal data on your device.
While VPN software isn’t specifically designed to guard against malware, the firewall of a VPN can help block port forwarding, thereby preventing unauthorized access to your device. This provides a certain level of protection against malware, making Onion over VPN a safer option than using Tor alone.
Security Against Traffic Correlation Attacks
Traffic correlation attacks involve third parties monitoring your traffic to find a link between the data entering and leaving your network.
By analyzing the timing, behavior, and volume of traffic, it’s possible to identify the websites you’re accessing at specific times. Using Onion over VPN can help protect against complete de-anonymization, as your actual IP address is concealed by the VPN software.
However, if a government or state agency is conducting the traffic correlation attack, they can legally compel your VPN service to surrender any records associated with the VPN IP address.
If your VPN service maintains connection logs, these could potentially be matched to your identity. This underscores the importance of choosing a VPN service that only logs essential data.
Prevention of UDP Data Leaks
Tor is limited to supporting the TCP protocol, which implies that UDP traffic, including Voice-over-IP, must travel outside the Tor network. This could potentially expose your IP address and online activities to third parties, a situation referred to as “bad apple” attacks.
However, using Onion over VPN can offer a layer of defense against such attacks. Any leaked UDP traffic would still be channeled through the VPN server within an encrypted tunnel, preventing it from being used to identify you.
Nevertheless, data leaks can occur if the VPN connection is disrupted. Therefore, it’s crucial to comprehend which traffic can traverse the Tor network and adjust your online behavior accordingly.
Accessing Tor in Geographically Restricted Countries
While the use of Tor is legal in many countries, it is prohibited in certain regions, including Belarus, Turkey, and China.
VPN software provides users with the ability to conceal their actual location by establishing a connection to a VPN server in a different country. This means that you can use a VPN to download and use the Tor browser even in countries with stringent censorship.
However, some websites block traffic originating from Tor IP addresses, which could pose challenges in accessing certain services via Tor. To circumvent this issue, using a VPN over Tor could be a more effective solution.
Determining When to Use Onion Over VPN
Onion over VPN is typically suggested for individuals who are transmitting highly confidential information and could benefit from an extra layer of encryption. This setup can be particularly useful for whistleblowers and journalists in countries with high levels of censorship, as it allows them to circumvent geographical restrictions and access the Tor Network.
Consider using Onion over VPN if:
- Maintaining anonymity is your top priority
- You’re unable to directly access the Tor Network
- You’re a journalist, whistleblower, or activist
On the other hand, Onion over VPN may not be suitable if:
- You’re casually browsing the internet
- You’re visiting websites that require identification (e.g., social media)
- Connection speed is a critical factor for you
While this method can safeguard your device from ransomware and traffic correlation attacks, it doesn’t offer protection against malicious exit nodes. Therefore, caution is advised when using Tor. Due to the negative impact on connection speeds, this method is not recommended for casual internet users.
Keep in mind: absolute anonymity is unattainable. VPNs don’t provide complete anonymity, and your VPN service can technically detect your use of the Tor browser. Essentially, you’re transferring your trust from your ISP to your VPN.
The worthiness of Onion over VPN is thus situational. While the setup does offer some additional privacy and security, it can’t shield you from malicious actors within the Onion network.
Guide to Using Onion Over VPN Safely
If you choose to use Tor over VPN, this section will guide you on how to do so safely.
Setting up Tor over VPN is quite straightforward. You just need to establish a connection to your VPN before starting the Tor browser.
Here are the steps to safely set up Tor over VPN:
1. Subscribe to a VPN service that doesn’t keep logs, or select from our list of the best VPNs for Tor. We suggest using Private Internet Access with Tor as it offers a zero-logs policy, fast speeds, and reasonable pricing.
2. Connect to a VPN server. Choose a remote VPN server and connect to it. The closer the server is to your actual location, the faster your connection speeds will be.
3. Download the Tor Browser from the official Tor website.
4. Click on your device’s icon and follow the installation prompts to automatically install the Tor Browser on your device.
5. Launch the Tor Browser while still connected to the VPN server.
6. Browse anonymously. While browsing, it’s crucial to avoid visiting websites that could compromise your anonymity. This includes logging into personal online accounts or sending emails.
Comparing Tor Over VPN and VPN Over Tor
The Tor Browser and VPN software can also be utilized in the reverse order. In this scenario, you initiate the Tor browser before connecting to a VPN. This method, known as VPN over Tor, is the inverse of Onion over VPN.
With VPN over Tor, your traffic is first routed through the Tor network, and then it is directed through the encrypted VPN tunnel. Unlike Onion over VPN, exit nodes cannot view the content of your traffic, but guard nodes can see your actual public IP address.
The Tor Project advises users against using VPN over Tor as it can compromise your anonymity.
Below is a table to help you understand the advantages and disadvantages of using VPN over Tor:
| Advantages | Disadvantages |
| Protection from malicious exit nodes | Guard node can see your public IP address |
| VPN kill switch prevents data leaks | Setup is complex |
| Access to websites that block exit nodes is still possible for Tor users | Choice of VPN service is limited |
| Connection speeds are extremely slow | |
| Double encryption is excessive | |
| Your VPN service can theoretically monitor activity | |
| ISP can see you are connected to Tor |
Setting up VPN over Tor is complex and offers less anonymity than Onion over VPN. Assistance from your VPN service is necessary, which means your choice of VPN will be limited.
We advise against setting up VPN over Tor unless you have technical expertise. An incorrect setup can lead to traffic leaks, potentially compromising both your anonymity and security.
Here’s a summary of how VPN over Tor impacts your privacy and security:
Monitoring Capabilities of Your VPN Service
The Tor project advises against the use of VPN over Tor as it allows your VPN provider to access both your IP address and the contents of your web traffic, thereby undermining Tor’s main objective: total anonymity.
Certain VPN services maintain logs of your online activities. If you use one of these VPN services after connecting to Tor, your online activities will be completely traceable.
Risk of Being Flagged for Surveillance
If you initiate a connection to Tor prior to connecting to a VPN, the Tor guard node will be able to see your public IP address. Although it can’t decode the contents of your web traffic, this setup is less private.
Without first establishing a connection to a VPN server, your Internet Service Provider (ISP) will be able to detect your use of Tor. This could potentially flag you for surveillance by government agencies, including the National Security Agency (NSA).
The NSA collects and stores the IP addresses of numerous Tor users. This data is gathered by XKeyscore, a computer system developed by the NSA for the purpose of analyzing online activity.
Protection Against Malicious Exit Nodes
While VPN over Tor has its limitations in terms of privacy and anonymity, it does offer an added layer of protection against malicious exit nodes.
In contrast to Onion over VPN, if you connect to a VPN after accessing Tor, the Tor exit nodes won’t be able to view your data. The VPN encrypts all traffic from the exit node to the internet, meaning the exit node will know you’re using a VPN, but won’t be privy to the websites you’re visiting.
If your VPN connection gets disrupted, a kill switch will sever your device’s internet connection. This prevents your IP address and other sensitive data from being exposed. These combined measures significantly reduce the likelihood of third parties exploiting your information via malicious exit nodes.
Access to Websites Blocking Tor Traffic
When using VPN over Tor, websites that typically block Tor IP addresses become accessible. These websites receive your decrypted traffic from the VPN server, which means they won’t be able to see the IP address of the Tor exit node. Consequently, you can access websites that are typically inaccessible when using the Tor Browser.
How Double VPN Differs from Onion Over VPN
Also referred to as “multi-hop VPN”, Double VPN is an advanced feature provided by some VPN services for enhanced security. Essentially, it directs your traffic through two distinct VPN servers instead of just one.
NordVPN’s Double VPN feature can be found in the protocol menu.
While Double VPN and Onion over VPN may seem similar, they have structural differences. Onion over VPN connects users to two different types of anonymity software, while Double VPN routes your traffic through the same type of software, but twice.
Here’s a rundown of the key similarities and differences between Double VPN and Onion over VPN:
Similarities:
- Both Double VPN and Onion over VPN significantly slow down connection speeds.
- Both setups encrypt your web traffic multiple times.
- Onion over VPN conceals your IP address from the guard node, while Double VPN hides your IP address from the second VPN server.
Differences:
- Onion over VPN employs two types of anonymity software: VPN software and the Tor Browser. Double VPN uses only VPN software, which centralizes your risk.
- Onion over VPN encrypts your data four times, whereas Double VPN does so twice.
- Double VPN supports both the UDP and TCP protocol, while Onion over VPN supports only the TCP protocol.
- You can’t access the dark web or .onion websites with Double VPN. Onion over VPN allows access to the dark web.
Like Onion over VPN, Double VPN is designed to mask your online activity from your ISP and other intrusive third parties. It encrypts your data twice, significantly impacting your connection speeds.
In the Double VPN setup, the second VPN server only sees the IP address of the first VPN server. While some users view this as an additional layer of protection, it’s largely unnecessary for most users.
Conclusion
In conclusion, understanding “What Is Onion Over VPN“ is crucial for anyone concerned about online privacy. This technology offers a robust solution to keep your internet activities anonymous and secure. We hope this blog has shed light on its importance and functionality. For more insightful content, don’t forget to explore other article from Twistory. Always update good and useful information.
See more related articles:
1. How to Set Up a VPN on Roku: Step-by-Step Instructions


