If you’re aiming to navigate the digital world without leaving a trace or intending to gather data at scale without being blocked, a top-tier proxy is your go-to tool. It conceals your identity, enables access to geographically restricted content, and ensures you evade intricate anti-scraping measures set up by websites.
With a plethora of proxies available, including anonymous, transparent, shared, and reverse, it’s crucial to comprehend the unique features of each before selecting the one that best suits your business requirements.
This article will shine a spotlight on distorting proxies. We’ll delve into their nature, operational mechanism, and ascertain whether they align with your specific needs.
What is a Distorting Proxy? What is the role of a Distorting Proxy?
A distorting proxy is a specialized type of proxy server that operates as an intermediary between your device and the wider internet. Its fundamental role is to obscure your authentic IP address by altering the HTTP headers and supplying a fabricated one to the destination server. Consider it akin to a digital disguise for your online persona, facilitating a heightened level of anonymity as you navigate the web. This mechanism not only provides an additional layer of privacy but also allows for bypassing geographical restrictions on certain websites. It’s a powerful tool in the realm of online security and data privacy.

A Distorting Proxy performs several pivotal roles, primarily centered around:
Augmented Privacy
It veils your authentic IP address by altering HTTP headers, thereby making it challenging for websites and online trackers to pinpoint your identity and location. This provides a shield for your online browsing activities, protecting you from potential prying eyes.
Circumventing Geo-Restrictions
It empowers you to access websites and content that are geographically restricted in your region by presenting a counterfeit IP address from a different locale. This broadens your access to information and resources across various geographical territories.
Web Scraping
It facilitates the extraction of data from websites without being blocked. By rotating IP addresses with each request, the proxy significantly reduces the risk of detection and subsequent blocking by the website.
Security Fortification
It provides an extra layer of defense against targeted cyber-attacks and malevolent actors. By concealing your real IP address, it makes it arduous for hackers or other threats to trace or directly attack your device.
Online Liberty
It enables you to access information and resources that might be censored or restricted in your country, thereby contributing to greater individual autonomy and freedom of expression in the digital world.
The main difference between a Distorting Proxy and other types of proxies
While all proxies serve as intermediaries between your device and the internet, distorting proxies stand out due to their unique role in manipulating information. Here’s a comparative analysis of the main differences:
| Aspect | Distorting Proxy | Other Proxies (e.g., HTTP Proxy) | Anonymous Proxy |
| Transparency | Opaque – actively modifies HTTP headers to hide your real IP address and display a fake one. Websites see the proxy’s IP, not yours. | Transparent – simply forwards your request with the original IP address intact. Websites know you’re using a proxy but don’t know your personal information. | Semi-public – hides your IP from most websites but may reveal it to certain services or upon closer inspection. |
| Focus | Distortion – prioritizes hiding your identity by displaying misleading information (IP, headers). | Connectivity – primarily provides alternative connection points for better speed, security, or access control. | Content Filtering – often used by companies to manage internet access for employees. |
| Applications | Activities focused on privacy such as bypassing geographical restrictions, data collection, protection against targeted attacks. | Load balancing, improving connection speed, bypassing regional censorship (may not be fully anonymous). | Balances privacy with functionality, ideal for activities like safely accessing public Wi-Fi. |
| Legality | Usage may be restricted or illegal depending on local laws and terms of service of the target website. | Generally legal, but specific use cases like copyright infringement may be subject to legal scrutiny. | Typically used in organizational settings with legal issues resolved internally. |
How a Distorting Proxy works
A distorting proxy, also referred to as an IP spoofing proxy, is a specific type of proxy server that bolsters online privacy and security by concealing your genuine IP address. Here’s an in-depth look at its operation:
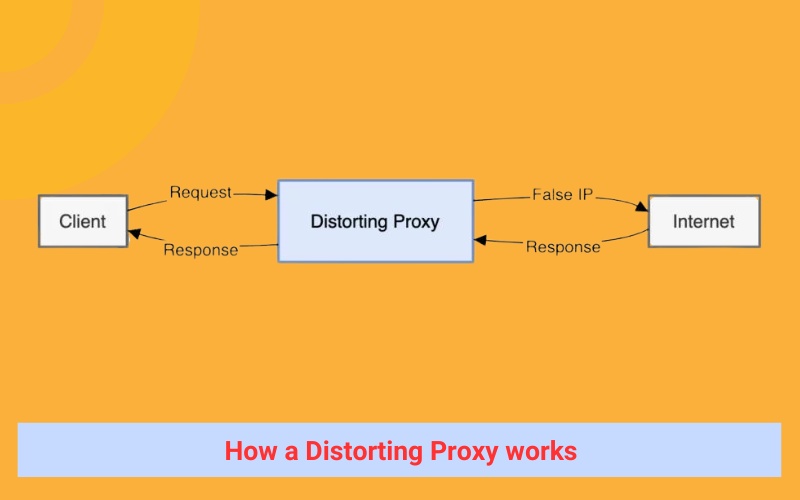
Interception of Request
When you dispatch a request to a website, it’s initially intercepted by the distorting proxy server. Consider it as an intermediary between your device and the internet.
IP Address Obfuscation
The proxy server then obscures your original IP address by substituting it with a distinct, typically temporary, IP address from its own repository. This new IP address could originate from any geographical location worldwide.
Modification of HTTP Headers
The proxy server further modifies the HTTP headers of your request. These headers encapsulate information about your device and connection, including your real IP address. The proxy amends these headers to mirror the counterfeit IP address it allocated.
Forwarding of Request
With your IP address obfuscated and headers modified, the proxy server forwards your request to the intended website. The website perceives the fake IP address and presumes it’s originating from the proxy server, not your device.
Relaying of Response
The website reciprocates by sending its response back to the proxy server. Ultimately, the proxy server receives the response and forwards it to your device, thereby completing the communication loop.
Exploring the use cases of a Distorting Proxy
Distorting proxies, with their unique ability to mask a user’s IP address and alter HTTP headers, offer several benefits across a range of online activities. Let’s explore some of the primary applications:

Using a Distorting Proxy to protect identity
- Online Privacy: Distorting proxies enhance online privacy by hiding your actual IP address, making it challenging for websites, trackers, and even your Internet Service Provider (ISP) to associate your online activities with your identity. This can help protect your personal information and browsing habits.
- Circumventing Censorship: In regions with internet restrictions, distorting proxies can be employed to access blocked websites and services by creating an illusion that you’re connecting from a different location.
- Anonymity in Online Forums and Chats: When participating in online discussions, a distorting proxy can help safeguard your identity and mitigate the risk of targeted harassment or doxing.
Accessing location-restricted content with a Distorting Proxy
- Geo-Blocked Content: Numerous websites and streaming services limit access based on a user’s geographical location. By deploying a distorting proxy in an allowed region, you can circumvent these restrictions and access content that might otherwise be inaccessible.
- Price Discrimination: Some online retailers display different prices or product availability based on a user’s location. A distorting proxy can enable you to access better deals or products that might be restricted in your region.
Leveraging a Distorting Proxy for caching purposes
- Bandwidth Reduction: Distorting proxies can cache frequently accessed content, reducing the necessity to repeatedly download identical data from the original server. This can decrease bandwidth usage, potentially enhancing internet speed and reducing costs.
- Faster Load Times: By storing content closer to the end user, distorting proxies can significantly diminish loading times for websites and web applications, thereby improving the user experience.
Web scraping
- Data Collection: Distorting proxies can be utilized to amass large volumes of data from websites without disclosing your real IP address. This is crucial for web scraping activities, where excessive requests from a single IP address might be flagged or blocked.
- Market Research: Businesses often employ distorting proxies for web scraping to collect competitor pricing, product information, and market trends.
- Price Comparison: Travel websites and aggregators can leverage distorting proxies to gather pricing data from various airlines and hotel providers, enabling users to effectively compare costs.
Pros and cons of using a Distorting Proxy
Using a distorting proxy can have both advantages and disadvantages. Here are some pros and cons to consider:

Pros of using a Distorting Proxy
- Privacy Enhancement: Distorting proxies can substantially augment online privacy by concealing your authentic IP address and other identifiable information from websites and online services. This makes it arduous for third parties to track your online activities, gather your personal data, or target you with personalized advertisements.
- Circumventing Censorship: They can frequently be employed to bypass internet censorship and access blocked content. By channeling your traffic through a server in a disparate country, you might be able to access websites and services that are restricted in your region.
- Security Amplification: Distorting proxies can append an extra layer of security to your online activities by encrypting your traffic and making it challenging for hackers to intercept and pilfer your data.
- Bypassing Geo-Restrictions: They can be utilized to circumvent geo-restrictions on websites and services, enabling you to access content that is not available in your country. For instance, you could employ a distorting proxy to view a video on a streaming service that is exclusively available in the United States.
- Avoiding Price Discrimination: Distorting proxies can assist you in evading price discrimination by creating an illusion that you are located in a different region. This can be beneficial for securing better deals on flights, hotels, and other goods and services.
Cons of using a Distorting Proxy
- Speed Reduction: Distorting proxies can occasionally decelerate your internet connection due to the additional routing and encryption overhead.
- Reliability Concerns: Some distorting proxies may be unreliable or experience frequent downtime.
- Security Risks: If you opt for an untrustworthy proxy provider, your traffic could be intercepted and scrutinized by the proxy operator.Website Blocking: Some websites may block access from known distorting proxy servers.
- Legal Implications: In some countries, using a distorting proxy to circumvent censorship or access blocked content may be deemed illegal.
Hidden risks of distorting free proxy lists
While free distorting proxy lists may appear as an alluring method to enhance your online privacy and access blocked content, they frequently harbor hidden risks that can eclipse the potential advantages.
Malware and Spyware
Free proxy lists are infamous breeding grounds for malware and spyware. Cybercriminals can inject malicious code into these lists, which subsequently gets installed on your device when you utilize the proxy. This can grant attackers access to your personal information, financial data, and even command over your device.
Data Interception and MitM Attacks
Free proxies often lack robust encryption, rendering your traffic susceptible to interception and manipulation by third parties. This implies that anyone situated between you and the website you’re visiting can potentially view your data, inclusive of passwords and sensitive information. This vulnerability also paves the way for Man-in-the-Middle (MitM) attacks, where cybercriminals can intercept and tamper with your communication.
Botnets and Spam
Free proxy lists are routinely exploited by botnets and spammers to disguise their identities and disseminate malicious content. If you employ a proxy on such a list, your IP address could be associated with these activities and get flagged by security systems, potentially resulting in your own account being blocked or suspended.
Unreliable Performance and Downtime
Free proxies frequently suffer from unreliable performance due to overloaded servers and scarce resources. This can result in slow connection speeds, recurrent disconnections, and inconsistent performance, rendering them unsuitable for activities like streaming or online gaming.
Legal Ambiguities
The use of free proxies to circumvent geo-restrictions or access blocked content can occasionally be illegal, contingent on your location and the specific content you’re endeavoring to access. Unwittingly violating these laws could lead to penalties or even legal repercussions.
Conclusion
The fundamental premise of distorting proxies, which involves providing a user with a fabricated IP address to maintain anonymity online, indeed appears to be an effective solution. However, these proxy servers also possess significant drawbacks that could potentially inflict more harm than benefit to you and your organization in the long run.
While these proxies are capable of handling simpler tasks (e.g., preserving your identity during online research), we still advocate for the selection of premium proxies, such as residential or datacenter ones. These are more suitable whether your intention is to execute intricate web scraping tasks or merely to browse the internet securely.
For more interesting and useful information, don’t forget to visit twistory.net! This is a treasure trove of knowledge on many different topics. If you have any questions or require further details, please ask. We are here to assist


