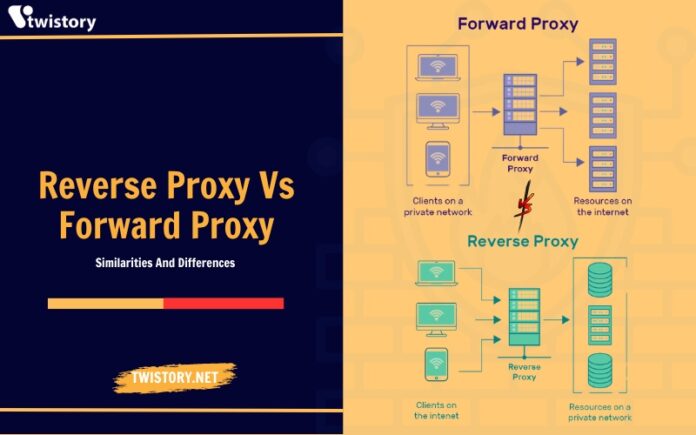
There is a common confusion in many businesses regarding the specific roles and differences between forward proxies and reverse proxies. This article aims to demystify these concepts by closely examining “Reverse Proxy vs Forward Proxy”. We will dissect the unique functions of each and demonstrate how administrators can leverage reverse proxies for efficient control over access management, highlighting the distinct purposes they serve in network traffic routing and security.
1. What Is a Forward Proxy? How Does It Work?
A proxy server, often referred to as a forward proxy, acts as an intermediary, facilitating the flow of data between a client or multiple clients and another system, typically located outside the local network. This server plays a crucial role in controlling traffic flow based on established rules. It has the ability to transform and conceal client IP addresses, implement security measures, and filter out unrecognized traffic.
In environments like business organizations or data centers, where networks are shared, proxy servers are a common feature. These servers present a unified interface for client interactions, removing the need for individual clients to handle complex policy enforcement and routing decisions.
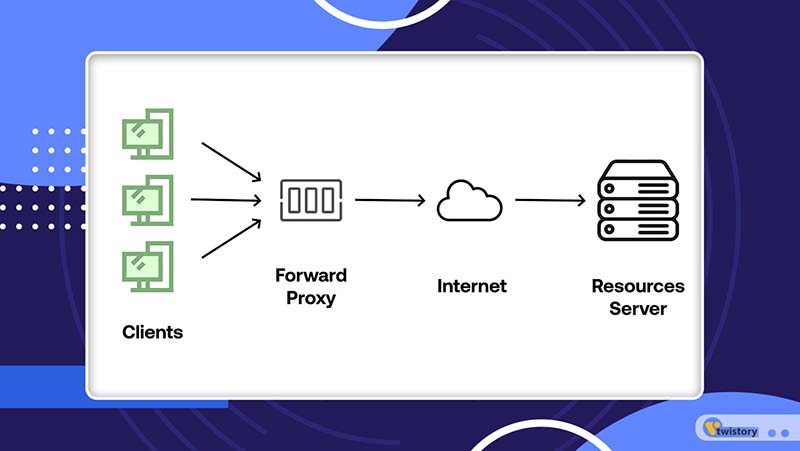
Consider a scenario where a user within a private network makes an online request. This request first travels through the forward proxy server before reaching the desired web page. The server then retrieves the data from the website and relays it back to the proxy. Subsequently, the proxy forwards this data to the user. This process creates an illusion that the request originates from the proxy server itself, effectively masking the user’s original IP address.
2. Common Types of Forward Proxies
In the realm of forward proxies, there are several distinct types, each characterized by their location or the specific areas they serve. Understanding these differences is key to selecting the right proxy for your needs.
2.1 Residential proxy
Originating from an Internet Service Provider (ISP), a residential proxy effectively conceals the actual physical location of a user. It allows users to choose a specific location, like a country or city. Since these proxies are linked to a real-world address, they make it seem as if the user is accessing the internet from that selected area.
2.2 Datacenter proxy
Typically utilized by businesses, datacenter proxies are not sourced from ISPs. Instead, they generate IP addresses from their own pool or from third-party cloud providers. This type of proxy offers a distinct advantage in terms of speed and reliability, as they are housed in data centers with robust infrastructure.
2.3 Mobile proxy
Contrary to what the name might imply, a mobile proxy doesn’t cater exclusively to mobile devices. Rather, its IP addresses originate from a mobile network. Unlike residential or data center proxies that have a fixed source, mobile proxies give the impression of accessing the internet via a mobile data network. This characteristic is sometimes exploited by cybercriminals and scammers for its ability to mimic a mobile user’s internet behavior.
3. Applications of Forward Proxy
Forward proxies serve a variety of important applications in both corporate and individual network environments. Here are some of the key applications of forward proxies:

3.1 Security and Data Management
Forward proxies play a crucial role in enhancing network security by scrutinizing all web requests. This scrutiny allows them to sift out hazardous responses and thwart unauthorized website access. A forward proxy is particularly adept at detecting and halting network traffic that inadvertently transmits private information to unintended recipients. By obscuring an organization’s network structure and shielding its weak points, a forward proxy prevents malicious entities from identifying and exploiting these vulnerabilities.
3.2 Circumventing Web Filters and Restrictions
Many websites use IP-based geolocation to pinpoint a user’s location, often leading to content restrictions based on that geographic location. This can result in limited access for users in certain regions. Forward proxies address this issue by masking the user’s IP address, enabling them to bypass web filters, which often include anti-proxy measures. This allows users to access geo-restricted content and browse the internet anonymously, safeguarding their privacy and evading tracking mechanisms.
3.3 Blocking Malicious Access
Given the extensive range of assets that need protection behind a proxy server, an extra layer of defense is necessary. Companies cannot allow unrestricted employee access to every online resource and private website. By configuring a forward proxy, organizations can limit access to specific websites and content, thereby preventing employees from accessing potentially harmful or non-compliant sites. If an employee attempts to reach these restricted websites, the forward proxy intervenes, blocking the request and ensuring the integrity and security of the network.
4. Benefits and Limitations of Forward Proxy
Forward proxies are pivotal in bolstering online security and privacy, serving as a bridge between users and the digital world. Grasping the benefits and limitations of forward proxies is key to making well-informed decisions regarding their use.
4.1 Benefits of Forward Proxy
- Enhanced Security: Forward proxies stand as a shield between users and the web, screening out harmful content and adding an extra layer of protection against digital threats.
- Access Control: They empower organizations to regulate and limit access to certain websites, aiding in the enforcement of corporate policies and the management of internet usage.
- Bypassing Geo-Restrictions: These proxies facilitate access to region-locked content by channeling traffic through servers located in various parts of the world.
- Improved Network Performance: By storing frequently accessed content, forward proxies can quicken loading times, boosting overall network efficiency.
4.2 Limitations of Forward Proxy
- Latency and Speed Impact: Using this proxy can cause latency, affecting internet speed, especially if the proxy server is geographically far away from the user.
- Configuration Complexity: The setup and configuration of forward proxies can be intricate, especially in large-scale networks, necessitating careful planning and thorough documentation.
- Risk of Misuse: There’s a potential for forward proxies to be exploited for harmful activities, like circumventing security protocols or engaging in unauthorized access.
- Dependency on Server Availability: The functionality of forward proxies hinges on the consistent operation and dependability of the proxy servers. Any disruptions in these servers can lead to internet access issues for users.
5. What Is a Reverse Proxy? How Does It Work?
A reverse proxy, a specialized type of proxy server, operates differently from its traditional counterpart. While the classic proxy server is designed to safeguard clients, a reverse proxy focuses on the protection of servers. It acts as an intermediary, receiving client requests, routing them to various servers, and then delivering the server’s response back to the client as though the proxy itself fulfilled the request. The client remains unaware of the actual server processing its request, interacting solely with the reverse proxy.
In contrast to a traditional forward proxy that facilitates multiple clients in accessing an external network, like a business proxy routing and filtering employee internet traffic, a reverse proxy caters to multiple servers. It stands as a crucial junction point between clients, users, and application servers, taking charge of access policy management, traffic routing, and concealing the identity of the server that processes the request.
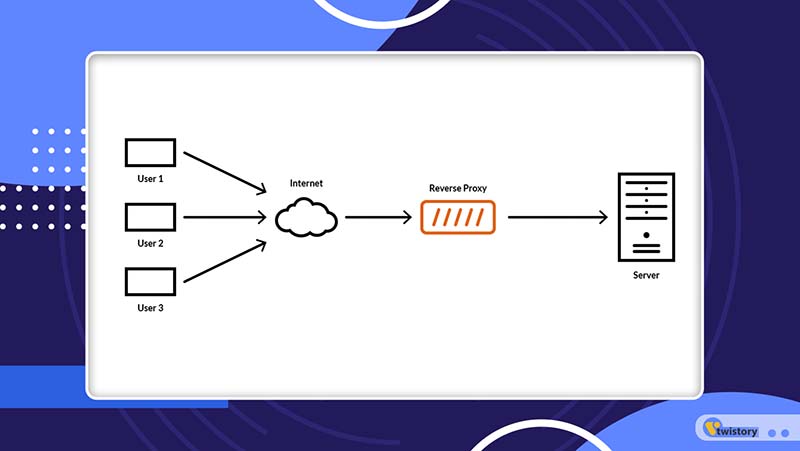
The operation of a reverse proxy involves directly accepting requests from users, identifying the most suitable server, and then passing the client’s request onto that server. The backend server then handles the request and sends its response to the proxy, which in turn forwards it to the client. This mechanism significantly enhances a website’s performance, security, and scalability.
In the context of a reverse proxy, a load balancer plays a pivotal role. It evenly distributes incoming requests among backend servers, evaluating their availability, and assigning the most appropriate server to handle each user request.
6. Common Types of Reverse Proxies
Reverse proxies, while sharing a common core function, can be categorized into two primary types based on their distinct features: regular reverse proxies and load balancers. Both play vital roles in network architecture but serve different purposes.
6.1 Regular Reverse Proxies
These proxies act as intermediaries between a client and a server. They receive a request from a client, forward it to the server for processing, and then relay the server’s response back to the client. The primary use of regular reverse proxies is to enhance security. They shield the identity of backend servers, offering protection against potential cyber threats.
6.2 Load Balancers
A specific subtype of reverse proxies, load balancers, do more than just relay requests and responses. They distribute incoming traffic across multiple backend servers. This distribution is key to managing the client-server communication across various servers. The primary objective of load balancers is to allocate workload evenly among servers, thereby boosting speed and efficiency, and preventing any single server from becoming a bottleneck.
7. Applications of Reverse Proxy
Reverse proxies are versatile and have numerous applications, including:

7.1 Caching
A key function of a reverse proxy is its ability to cache data. Modern websites often contain numerous images and videos, which can significantly impact their performance. By caching this data, a reverse proxy lightens the load on web servers, leading to quicker load times and a smoother user experience.
7.2 Load Balancing
For websites experiencing high traffic volumes, a reverse proxy is essential in managing the influx of requests. It evenly distributes incoming traffic across several backend servers, enabling businesses to handle numerous requests simultaneously. This feature of a reverse proxy not only enhances the website’s capability to serve more users but also contributes to a more efficient and stable online presence.
7.3 Anonymity
Moreover, a reverse proxy adds a layer of anonymity to the central web server. By intercepting all requests and directing them to an external server, the central server’s identity remains hidden from clients. This obscurity is a strategic advantage, shielding the server from potential security breaches and deterring malicious actors.
8. Benefits and Limitations of Reverse Proxy
Reverse proxies offer several benefits and advantages in various scenarios, but they also come with certain limitations and considerations. Here’s a breakdown of the benefits and limitations of using a reverse proxy:

8.2 Benefits of Reverse Proxy
- Client Request Forwarding: It forwards client requests to destination servers while maintaining opacity regarding the back-end operations. This means clients are unaware of the internal processes taking place on the server side.
- Load Balancing: Requests are evenly distributed across multiple server clusters or replicated servers. This not only improves service availability but also reduces latency, particularly when using content delivery networks (CDNs).
- Enhanced Security: A significant security feature is that SSL encryption terminates at the reverse proxy level. This setup enables the proxy to function as an effective web application firewall (WAF), relieving destination servers of the need to handle SSL directly.
- Optimized Response Times: Administrators can implement caching and compression techniques closer to the clients, resulting in faster response times.
8.3 Limitations of Reverse Proxy
- Resource Requirements: Operating a reverse proxy demands additional network resources and processing power. When setting up virtual hosting, resources must be allocated between public and private ports, leading to extra hardware requirements.
- Troubleshooting Challenges: The lack of direct visibility into client requests and the content flowing through the reverse proxy can complicate troubleshooting, especially during production deployments.
- Potential Latency: Reverse proxies can introduce latency in transactions. They may also constrain performance by limiting options for load balancing and content delivery.
9. Comparing Reverse Proxy vs Forward Proxy: Similarities and Differences
Forward proxies and reverse proxies are intermediary servers in networking and web-related tasks. Although they share some functions, their primary purposes and operational directions differ significantly. Let’s explore the similarities and differences between these two types of proxies:
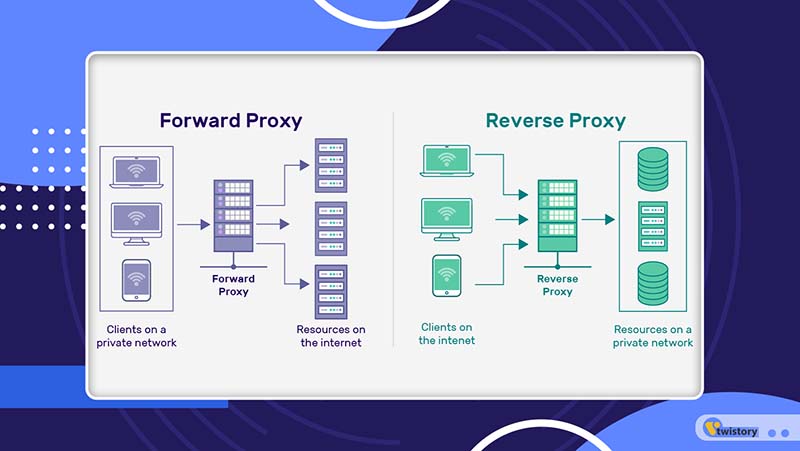
10. Similarities Between Reverse Proxy vs Forward Proxy
The most notable similarity between forward and reverse proxies lies in their role as protective barriers for devices connected to private networks against external network threats.
- Security Functions: Both types of proxies can regulate the types and sizes of files that pass through them, adding a layer of security. They also have the capability to require user authentication before allowing request transmissions.
- Port and Protocol Switching: Forward and reverse proxies can execute port and protocol switching, further camouflaging the access patterns to resources hidden behind them.
- Software Flexibility: It’s interesting to note that the same software can often be configured to function either as a forward or a reverse proxy. Nginx and Apache web server, for instance, are popular choices for reverse proxy setups in enterprise architectures. These software solutions can also be adapted to serve as forward proxies.
11. Differences Between Reverse Proxy vs Forward Proxy
Despite their similarities, reverse and forward proxies have distinct differences in functionality, implementation, and the level of protection they offer to private networks.
- Roles and Direction of Operation: A forward proxy stands between users and the servers they wish to access. It mediates user requests, forwarding them to the intended server, and then channels the server’s response back to the user. In contrast, a reverse proxy positions itself in front of servers, managing requests from users, directing them to appropriate servers, and then relaying the server’s response back to the user.
- Configuration and Usage: Forward proxies require manual configuration on digital devices within a workplace, such as laptops and smartphones, to secure web access. Reverse proxies, however, operate without the need for manual settings on individual user devices.
- Target Audience and Function: While forward proxies are primarily used by users within a network to safely access external web resources, reverse proxies focus on managing communication between external networks and backend servers.
12. Conclusion: Choosing Between Reverse Proxy Vs Forward Proxy
In conclusion, understanding the nuances of “Reverse Proxy vs Forward Proxy“ is essential for anyone involved in managing network infrastructures. While they share similarities in providing security and regulating data flow, their distinct roles and functionalities cater to different aspects of network management. Forward proxies focus on user access and security within the network, while reverse proxies excel in server protection and managing external communications. Grasping these differences is key to implementing the most effective proxy solution for your specific needs.
To discuss and explore such important technological concepts in more detail, don’t forget to visit our blog at Twistory. Our range of topics and expert insights will surely enrich your understanding of the ever-evolving digital landscape. Stay tuned for more informative and engaging content!
>>See more related articles:
1. Reverse Proxy vs API Gateway: Tech Duel Unraveled
2. API Proxy vs API Gateway: Unpacking the Essentials
3. Anonymous Proxy vs VPN: Key Differences