As our dependence on mobile devices for internet access grows, the importance of secure and efficient mobile browsing cannot be overstated. One key player in this domain is the mobile proxy.
In this piece, we will delve into the realm of mobile proxy, examining their mechanisms, applications, pros, cons, and how they stack up against other proxy types. By the conclusion of this article, you will possess a thorough grasp of mobile proxies and their significance in the current digital era.
Let’s dive in!
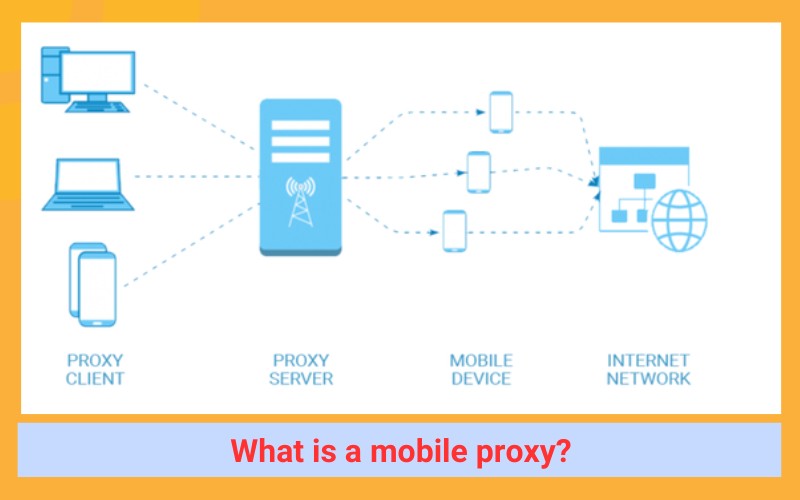
What is a mobile proxy?
A mobile proxy serves as a gateway that assigns a mobile IP address to a device, as opposed to a residential IP or a VPN. Essentially, mobile proxies create the illusion that the user is accessing the internet via a mobile data network, thereby concealing their actual address.
While this may seem like a minor deviation from residential proxies, the architecture of mobile data networks leads to significant differences behind the scenes. These differences make mobile proxies a more attractive option for individuals intent on committing illicit or illegal activities online.
It’s important to clarify that mobile proxies are named as such due to their use of a mobile network’s IP address. They are not necessarily operated on or allocated to mobile phones or other mobile devices.
Likewise, a mobile device like a smartphone does not possess a mobile IP if it’s connected to a residential network (for example, when connected to home Wi-Fi).
How does a mobile proxy work?
Similar to residential proxies, mobile proxies utilize gateway software on any device to allocate a specific type of IP to that device – an IP that is part of a mobile data network.
To access the internet, a mobile device initially connects to a mobile cell tower, where it is assigned an available IP. Multiple mobile IPs from the same network will connect via the same tower.
Interestingly, a mobile proxy can be used from a device that isn’t a mobile phone or tablet. This is possible as long as the proxy employs mobile hardware that allows their device to read a SIM card, such as a mobile dongle.
Since mobile IPs are distributed by the mobile network carrier, they have access to all IP addresses linked to this carrier, which can range in the thousands or even tens of thousands.
A key feature of mobile proxies is that the IPs they allocate are not unique, which can be advantageous for those seeking to conceal their online activities.
Types of mobile proxies include 4G and 5G mobile proxies, as well as rotating and dedicated mobile proxies.
How is a mobile proxy set up?
There are two main approaches to establishing a mobile proxy:
- Proxy providers develop software that, once installed, transforms a device into a mobile proxy node. This is typically done intentionally, although it’s possible to operate a proxy node unknowingly.
- SIM card farms, after amassing a number of SIM cards, establish proxies using mobile data dongles and suitable software.
Once these are set up, they are either sold to individuals interested in accessing the internet via a mobile proxy, or leased in return for goods or services, which are often of questionable legality.
Is a mobile proxy different from other types of proxies?
Indeed, mobile proxies exhibit distinct differences from other types of proxies, all of which stem from the manner in which cellular carriers assign IP addresses to mobile devices.
All of the following are methods for concealing one’s internet location/IP address. But how do they stack up against each other?
| Residential Proxy | VPN | Mobile Proxy | Tor | |
| Assigned IP type | Residential IP, presumed to be provided by a land-based traditional ISP | Static, non-unique | Mobile IP, presumed to be provided by mobile network | The end node’s IP |
| Proxy detectability | Medium-hard to identify as a proxy | Easy to identify as a proxy (known addresses) | Almost impossible to identify as a proxy | Moderately easy to identify (lists of known end nodes) |
| Uniqueness | Can request a dedicated IP, if needed | Can request a dedicated IP, if available | Can never be unique or private (IP address is always shared with others) | Cannot be unique (exit nodes ever-changing and shared with others) |
| IP reputation | Varies by residential proxy type | Medium IP reputation | Best IP reputation | Low IP reputation |
As evident from the comparison table, there are marked differences among various types of proxies, including residential proxies, mobile proxies, VPNs, and onion routing such as with Tor.
Why are mobile IPs assigned differently?
Due to the architectural design of mobile data networks, they do not allocate a unique IP address to each individual device.
During periods of high network load, the same IP address may be assigned to multiple mobile devices – potentially dozens or even hundreds, depending on the mobile network. This is a consequence of the IPv4 shortage and the implementation of carrier-grade NAT technology (CGN) to mitigate this issue on mobile data networks.
For instance, in 2019, Vodafone had 17.2 million active subscribers in the UK but only a total of 131,000 IP addresses available. These were shared among all 17.2 million of Vodafone’s users.
In other words, up to 131 users could have been sharing the same IP address during peak network load. While these figures fluctuate over time, the general principle remains:
On mobile data networks, the same IP address is assigned to hundreds of different devices. This makes mobile IPs less likely to be banned by websites and more appealing to fraudsters.
No one wants to risk banning a large number of users because one of them might potentially be engaging in criminal activity, so they will not ban someone based on their IP, regardless of their behavior.
Unsurprisingly, fraudsters are keen to exploit this…

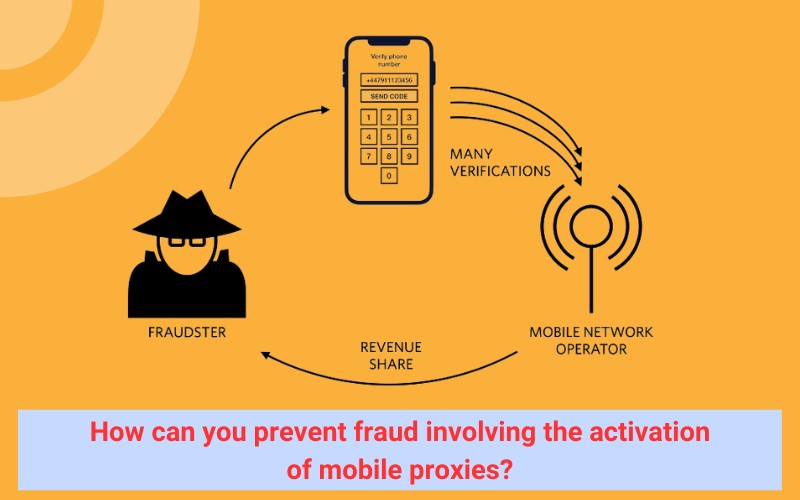
How is a mobile proxy used for fraud?
Tech-savvy fraudsters can employ mobile proxies to dodge detection and misrepresent their location when engaging in various types of fraudulent activities, ranging from card testing and arbitrage to auction fraud and more.
Mobile proxies serve as a means for fraudsters to conceal their activities, rather than a method to execute fraud, forming a part of their operational security (OPSEC).
This is largely due to the unique technical aspects of mobile proxies, as we discussed earlier. Websites and online services are cognizant of the fact that dozens, if not hundreds, of users can share the same IP with no other commonality besides their mobile carrier or mobile proxy provider. Consequently, they are hesitant to outright ban any mobile IPs, as this would prevent legitimate users from accessing their services, content, or even purchasing their products.

How can you prevent fraud involving the activation of mobile proxies?
Thwarting fraud enabled by mobile proxies necessitates a multi-faceted strategy, given the difficulty in detecting these proxies and their ability to evade conventional fraud prevention measures. Here are some tactics to consider:
Detection and Identification
- IP Reputation Services: Leverage services that evaluate the risk linked to IP addresses. Opt for services that specialize in detecting residential proxies used for nefarious purposes.
- Fingerprinting Techniques: Examine device-specific attributes such as browser language, time zone, fonts, and screen resolution. Deviations from normal user behavior can signal proxy usage.
- Behavioral Analysis: Keep an eye on user activity for unusual patterns like swift account creation, mass transactions, or atypical login locations.
Friction and Authentication
- Two-Factor Authentication (2FA): Incorporate 2FA for sensitive transactions and actions, adding an additional layer of verification beyond passwords.
- Challenge-Response Systems: Introduce dynamic challenges, like CAPTCHAs or puzzles, to distinguish humans from automated bots that rely on proxies.
- Device Binding: Associate accounts with specific devices, making it more difficult for fraudsters to operate from different proxies.
Risk Scoring and Decisioning
- Machine Learning and Scoring: Utilize machine learning models that analyze a mix of data points to evaluate fraud risk in real-time and make informed decisions.
- Adaptive Risk Thresholds: Modify risk thresholds based on real-time data and trends to stay one step ahead of evolving fraud tactics.
- Manual Review: Establish manual review processes for high-risk transactions or suspicious activity flagged by the system.
Conclusion
In conclusion, we have delved into the topic of “Mobile Proxy” – a crucial tool in today’s digital world. From its operation, applications, to related cybersecurity issues, we have provided a comprehensive view on this subject. However, this is just a small part of the vast field of information technology. Don’t forget to follow Twistory for more useful and interesting updates about the tech world. Thank you for reading!


