Even if the term “transparent proxy” is new to you, chances are you’ve encountered them unknowingly. This is because they are frequently used by web servers to scrutinize and filter incoming internet traffic. You might have come across transparent proxies at public Wi-Fi spots or within your workplace network, as they are an efficient tool for tasks such as user authentication, caching, load balancing, and content filtering.
In this article, Twistory will take a deep dive into the world of transparent proxies. We will explore their functions, their applications in business, and how they can be detected.
What is a Transparent Proxy?
A transparent proxy, often referred to as an inline, intercepting, or forced proxy, is a server that sits between an end-user or device and the internet, intercepting the connection. It earns its “transparent” moniker by operating without altering requests and responses. The Squid Transparent Proxy Server is a well-known open-source tool for transparent proxying.
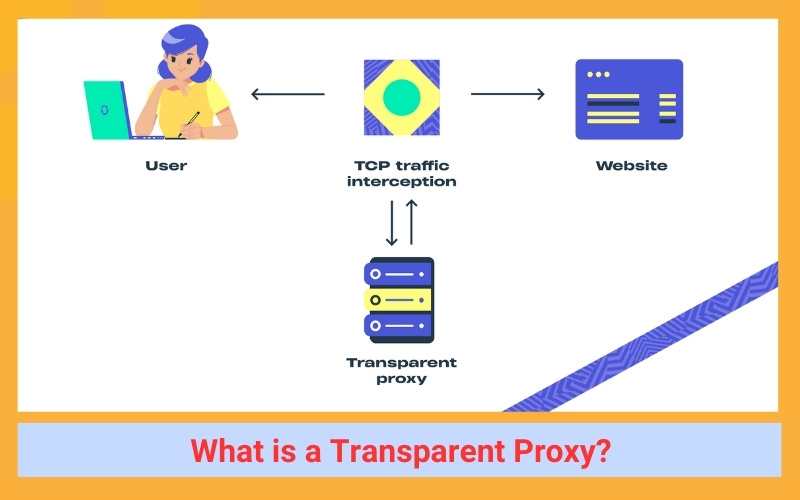
Consider a user browsing the internet on a corporate network. The user might request to read a news article on cnn.com, experiencing the same content as they would on their home connection.
However, what the user may not realize is that the news article is not delivered directly from the cnn.com origin server. Instead, it’s served via a transparent proxy on the corporate network. The user’s experience remains unchanged, but their employer gains the capability to monitor their online behavior and potentially restrict access to specific websites.
>>See more: What is a Private Proxy? Ultimate Guide for 2023
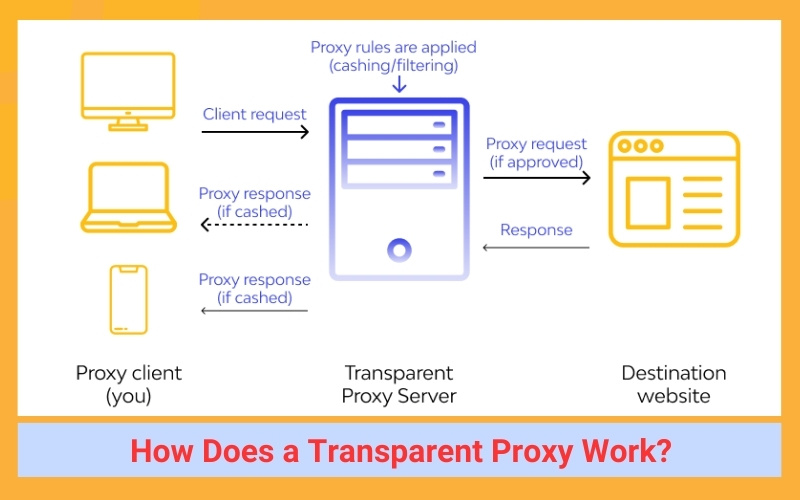
How Does a Transparent Proxy Work?
Firstly, a transparent proxy is configured by the web server itself. This is particularly useful for companies with substantial incoming traffic that needs to be monitored and controlled. It’s a convenient tool as it can be set up on a company network without necessitating further configurations on the client-side. In contrast, a non-transparent proxy requires adjustments to the settings on each client’s device, which can quickly become cumbersome.
Since transparent proxy servers don’t require any client-side setup, the client often remains unaware that a transparent proxy is intercepting the connection. This is why these proxies are termed ‘transparent’. They leave the client’s information (such as IP address and location) unchanged and visible to the destination server, while non-transparent proxies typically hide it.
Here’s a comparison:
| Transparent Proxy | Non-transparent Proxy | |
| Configuration | Once configured on the network, it handles incoming traffic automatically. | Needs to be configured on each device. |
| Privacy | The client’s IP address and geo-location are visible. | The client’s IP address and geo-location are concealed. |
| Awareness | The client is unaware of the proxy. | The client is aware of the proxy and usually sets it up. |
| Request modification | The proxy doesn’t modify the client’s requests. | The proxy modifies the client’s requests. |
To further illustrate, consider transparent reverse proxies. These proxies scrutinize clients’ internet traffic by intercepting their connection. They establish a connection with both the web server and the client, initiating a three-way handshake (TCP handshake) for each. However, this means that the web server perceives the origin IP address of the request as that of the proxy.
With certain configurations, a reverse proxy can operate in transparent mode, where the client’s IP serves as the source IP for the TCP connection. By revealing the client’s information, it becomes a transparent reverse proxy, not just a reverse proxy.
>> See more: What is a Mobile Proxy? How does it function and work?
Use Cases for Transparent Proxies
Applications of Transparent Proxies Now that we’ve established a solid understanding of how a transparent proxy operates, let’s delve into its various applications. We’ve already touched upon user authentication, but there are several other use cases:
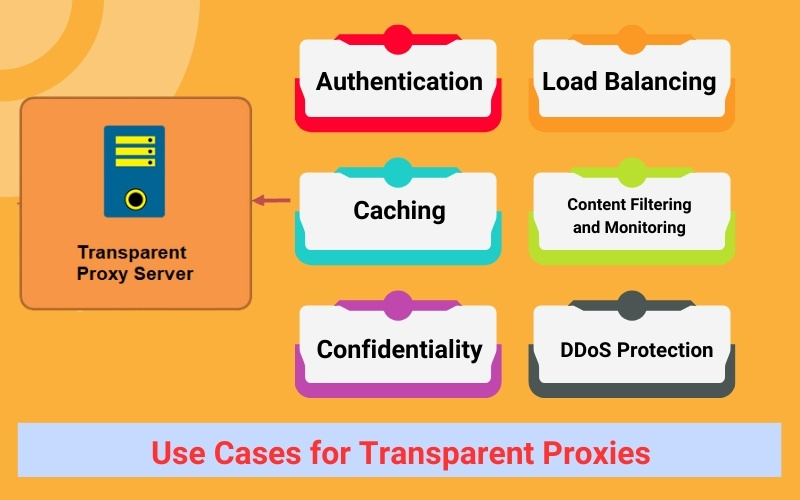
Authentication
As previously mentioned, transparent proxies can be instrumental in user authentication. Public Wi-Fi providers often utilize this to present users with their Terms and Conditions and authenticate visitors through registration. A transparent proxy can also monitor traffic and block connections that violate network rules.
Load Balancing
For high-traffic websites, transparent proxies can function as load balancers. A frequently accessed web server may distribute incoming traffic among multiple back-end servers, enhancing the website’s efficiency and speed.
Caching
Content Delivery Networks (CDNs) – networks of proxy servers spread across various locations – might employ transparent proxies to deliver data elements (like images, videos, etc.) more efficiently. They use a subtype of transparent proxies, known as caching proxies, to store information for future use.
This means that when someone requests content from a web server, the proxy stores it in its memory. The next time another person requests the same content, it’s delivered from the proxy server closest to the client’s location, not from the original server, thereby reducing latency.
Content Filtering and Monitoring
Companies commonly use this method to monitor employee online activity. They implement transparent proxies as filtering proxies to limit access from the internal network to undesirable online content (e.g., social media) and ensure fair network usage.
Confidentiality
An SSL proxy, a type of transparent proxy, can inspect HTTPS traffic and bolster security. An SSL proxy performs SSL encryption and decryption between the client and the server to prevent unauthorized interference.
DDoS Protection
In the realm of cybersecurity, transparent proxies can be incredibly beneficial. A type of transparent proxy (TCP intercept) can protect a web server against a distributed denial-of-service attack (DDoS). TCP intercept monitors all connections and replaces inactive ones with new ones when the number becomes excessive.
Advantages and Disadvantages of Transparent Proxies
Like any other digital tool, transparent proxies come with their own set of pros and cons.
Advantages of Transparent Proxies
- Enhanced Browsing Experience: Thanks to their caching capability, transparent proxies can significantly enhance the browsing experience. By caching, they can conserve upstream bandwidth and decrease loading times, thereby boosting performance.
- Simplicity of Implementation: One of the standout features of transparent proxies is their ease of setup, particularly when using renowned proxy tools like the Squid Transparent Proxy Server. Since transparent proxies are network-based, they can reroute multiple clients without the need for system reconfiguration on the client-side. This makes transparent proxies ideal web accelerators.
- Efficiency During Overload: Transparent proxies may outperform explicit proxies during instances of failure or overload. They possess an interception component that monitors the health of the proxies and swiftly takes action to resolve issues.

Disadvantages of transparent proxies
- Availability: Transparent proxies rely on network equipment and server operating systems for acceptance. Thus, those setting up transparent proxies need to be mindful of how modifications on the client-side could impact the proxy’s functionality.
- Network Issues: A transparent proxy must be correctly configured; otherwise, it can cause more problems than it solves. Indeed, a poorly configured transparent proxy can slow down the network and lead to connection drops.
- Data Risks: Selecting the appropriate protocol (as discussed in the section on SSL proxies) is crucial for security. Without it, your network could be vulnerable to malicious activities or data breaches. Individuals with the necessary expertise should thoroughly examine this topic before implementation.
How to Detect a Transparent Proxy?
By now, it should be evident that transparent proxies are quite prevalent, and there’s a good chance you’ve interacted with one without realizing it. You might be wondering if there’s a way to determine if your web requests are being routed through one. While it can be challenging, there are a few methods you can try.
One approach is to examine the HTTP response headers you receive from a website to see if any headers suggest the use of transparent proxies. This can be done by using the Inspect option in your browser and searching for HTTP headers such as X-Forwarded-For or Via. If this method is unsuccessful, you can try using a proxy detection site. Simply search for one using your search engine and select the one that seems most suitable.
However, it’s crucial to remember that these methods are not infallible, and even if these tests don’t uncover a transparent proxy, it’s still possible that you might be using one.
Conclusion
Proxies can significantly speed up and enhance web activity. They are a versatile tool that offers benefits to both clients and servers. From enhancing the browsing experience to providing greater control over network traffic, there are numerous ways in which businesses can leverage them to boost their operations.
In conclusion, a transparent proxy is a powerful tool with a wide range of applications. Its ability to improve browsing experiences, control network traffic, and provide security makes it an invaluable asset in today’s digital landscape. Don’t forget to follow Twistory.net, for more great, interesting, and useful content.


