Navigating the world of proxies can be as challenging as mastering a new language, with terms like SOCKS4, SOCKS5, HTTP, HTTPS, IPv4, and IPv6. Each protocol serves a unique purpose, and choosing the right one is crucial for your online activities. This comprehensive guide is dedicated to SOCKS5 proxies, providing you with a clear understanding of their functionality, advantages, and the scenarios where they excel. Whether you’re looking to enhance your privacy, bypass geo-restrictions, or improve network performance, SOCKS5 proxies are a versatile solution.
Continue reading to unlock the full potential of the SOCKS5 protocol and learn where to find the best providers for your needs. Discover the key differences between proxy protocols and make an informed decision on the best fit for you with our expert insights.
Understanding the Basics: What Are Proxies?
Embarking on the journey to understand SOCKS5 proxies begins with grasping the concept of a proxy server. Acting as a go-between for your device and larger networks like the internet, a proxy server is a pivotal player in online connectivity. By channeling your device’s requests through a proxy server, you’re not just connecting to the internet; you’re choosing a path that offers enhanced performance, privacy, and security. Proxies achieve this by adhering to specific network protocols—rules that dictate data transmission across devices.
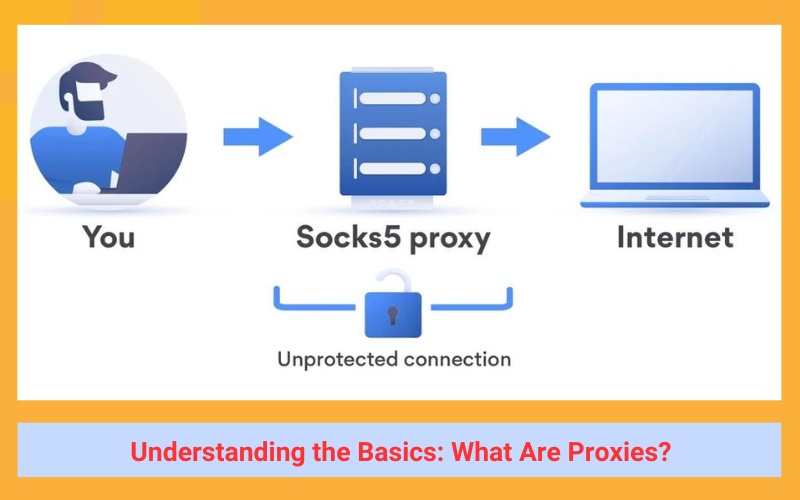
Here’s how proxies can elevate your online experience:
- Boost Performance: Proxies utilize caching to store frequently requested content, speeding up access and reducing load times.
- Safeguard Privacy: By masking your true IP address, proxies keep your online identity concealed.
- Secure Data: Encryption provided by proxies ensures your data remains unreadable during its journey across the internet.
Among the myriad of protocols and proxy types, the SOCKS5 (Socket Secure) protocol stands out. It’s not just another option; it’s a robust solution for those seeking a balance of anonymity and efficiency. If you’re already versed in the fundamentals of SOCKS5, the table of contents will guide you to the topics that pique your interest. Dive deeper into the world of proxies and unlock the full potential of your online activities with SOCKS5.
>>See more: What Is Proxy Server? How Does It Work & What Are Its Benefits?
Exploring SOCKS5 Proxies
A SOCKS5 proxy is a powerful tool that leverages the advanced capabilities of the SOCKS5 network protocol to facilitate seamless communication between clients and servers, even through stringent firewalls. By utilizing both Transmission Control Protocol (TCP) and User Datagram Protocol (UDP), a SOCKS5 proxy server adeptly transmits data to servers located beyond the firewall’s reach. It acts as a reliable intermediary, ensuring the smooth exchange of data without any interpretation, thus maintaining the integrity of the traffic. This attribute of SOCKS5 proxies makes them an ideal choice for clients restricted by firewalls from establishing direct TCP connections. Embrace the versatility of SOCKS5 proxies for unrestricted access and superior connectivity.

Defining SOCKS5 Proxies: What Sets Them Apart?
SOCKS5 proxies stand out in the digital landscape for their unique capabilities and performance enhancements. Here’s an SEO-optimized breakdown of their distinctive features:
- Versatile Protocol Support: Unlike other proxy types confined to TCP, SOCKS5 proxies boast compatibility with a diverse range of protocols, including TCP, UDP, and ICMP. This versatility opens up a broader spectrum of applications, making SOCKS5 a superior choice for various online activities.
- Enhanced Security with Authentication: Security is paramount, and SOCKS5 proxies deliver by offering configurable authentication measures. This added layer of security ensures that only authorized users can access the proxy, safeguarding against unauthorized intrusions.
- Dynamic Port Forwarding for Specialized Applications: SOCKS5 proxies excel in dynamic port forwarding, allowing traffic to be routed to any specified port on the destination server. This feature is particularly beneficial for specialized applications, such as online gaming, that require certain ports to function optimally.
- Accelerated Speeds for Efficient Data Transfer: Speed is a critical factor in proxy performance, and SOCKS5 proxies lead the pack. By transmitting data packets without alteration, they provide faster speeds compared to other proxies, ensuring efficient and swift data transfer.
The Inner Workings: How SOCKS5 Proxies Operate
The SOCKS5 protocol is a cornerstone of modern networking, enabling data to traverse networks securely and efficiently through the process of tunneling. This method involves segmenting data into packets for transport, which are then reconstructed upon arrival at their destination. Tunneling is adept at establishing robust connections, circumventing firewalls, and facilitating protocols otherwise unsupported on a network, with the option to utilize either TCP or UDP for transmission.
TCP vs. UDP: A Comparative Analysis
- TCP: Renowned for its reliability, TCP maintains a persistent connection until the complete transfer of data, ensuring ordered delivery and confirmed receipt.
- UDP: In contrast, UDP is a connectionless protocol, offering a swifter, more streamlined data transmission method. However, it lacks the ability to retransmit lost data or confirm delivery.
SOCKS5 and SSH Tunneling: Enhancing Security SOCKS5 proxies employ SSH tunneling to provide secure remote data transmission. This technique safeguards against data interception within the network by employing robust encryption and hashing algorithms.
The OSI Model and SOCKS5 Proxies Operating at the session layer (level 5) of the Open Systems Interconnection (OSI) Model, SOCKS5 proxies surpass other proxy types in protocol handling capabilities. They adeptly manage a variety of protocols, including HTTP, HTTPS, POP3, SMTP, and FTP, ensuring the integrity of data packets across diverse communication standards.
Comparing Protocols: SOCKS5 vs. SOCKS4
In the realm of proxy protocols, SOCKS4 and SOCKS5 represent two distinct versions, with SOCKS5 being the more advanced and secure iteration. The key differences between SOCKS4 and SOCKS5 lie in their security features: SOCKS5 incorporates encryption, authentication, and UDP support, enhancements absent in SOCKS4. These advancements render SOCKS5 not only more secure but also faster in performance.

SOCKS5 Protocol and Its Authentication Methods SOCKS5 stands out for its versatile authentication options, which include:
- Null Authentication: This method allows for connection to a proxy without any authentication, offering ease of access.
- Username or Password Authentication: Requires valid credentials for proxy connection, adding a layer of security.
- GSS-API Authentication: Both the client and server undergo authentication at the operating system level, ensuring a high degree of security.
Comparing Protocols: SOCKS5 vs. HTTPS
When it comes to proxy services, both SOCKS5 and HTTPS proxies are prevalent choices, each with its own set of advantages tailored to different requirements.
HTTPS Proxies: A Closer Look at Secure Data Transmission HTTPS, short for HyperText Transfer Protocol Secure, is the fortified version of HTTP, designed to encrypt data before it is sent across the internet. Its scope is narrower than that of SOCKS5, focusing solely on HTTP and HTTPS traffic, and it operates at the application layer—the seventh layer of the OSI model—which endows it with a higher level of functionality.
Key Distinctions of HTTPS Proxies
- Data Interpretation: HTTPS proxies have the capability to interpret data, which enables them to perform content filtering and caching. This can enhance security measures by eliminating superfluous or harmful data.
- Header Configuration: The ability to configure headers is another feature exclusive to HTTPS proxies. This is particularly useful in web scraping, as it grants more control and can help maintain anonymity by preventing digital fingerprinting.
SOCKS5 Proxies: Versatility Across Protocols In contrast, SOCKS5 proxies are protocol-agnostic, transmitting data without interpretation, which allows for a broader range of protocol support beyond just HTTP and HTTPS. This makes SOCKS5 proxies a more flexible option for those who require compatibility with various protocols.
Ultimately, the choice between SOCKS5 and HTTPS proxies hinges on the specific features you need: SOCKS5 for flexibility across different protocols, or HTTPS for a more feature-rich experience within the confines of HTTP and HTTPS traffic.
Benefits of a SOCKS5 Proxy
Unlock the full potential of your online activities with the unparalleled advantages of SOCKS5 proxies.
- Overcome IP Blocks: Navigate the web without restrictions, as SOCKS5 proxies enable you to bypass internet blocks effectively. Whether you’re accessing content from a different locale or circumventing censorship, SOCKS5 is your gateway to an open internet.
- Protocol Flexibility: Choose how you transport data with the option of TCP for reliability or UDP for speed. SOCKS5 proxies cater to diverse use cases, from large data transfers to maintaining consistent connections.
- Minimal Restrictions: The SOCKS5 protocol’s low-level, general nature means it’s compatible with all types of traffic and programs, offering you the freedom to use it across any network.
- Enhanced Performance: With SOCKS5 proxies, data packets are transmitted without header modifications, reducing the risk of mislabeling or misrouting. This efficiency is especially beneficial for P2P platforms, ensuring faster and more reliable data transport.
- Anonymity Meets Speed: Experience the best of both worlds with SOCKS5 proxies—enjoy the speed you need without compromising on security. They’re the ideal solution for those seeking a versatile, swift, and secure proxy service.

Practical Applications of SOCKS5 Proxies
SOCKS5 proxies are a versatile and powerful tool for various online activities, offering speed, flexibility, and a level of anonymity. Here’s a rewritten section highlighting their use cases:
For High-Demand Data Transfers
SOCKS5 proxies shine in scenarios that demand the transfer of substantial data volumes. They are perfect for peer-to-peer sharing, online gaming, and media streaming. Their ability to facilitate web scraping from data-heavy sources like video streams makes them invaluable for traffic-intensive tasks.
Circumventing Web Restrictions
SOCKS5 proxies enable users to access content restricted by geographical boundaries or government censorship. While they can bypass many firewalls, users should note that some advanced firewalls, especially those implemented by governments or ISPs, might still pose a challenge. Additionally, since header data isn’t encrypted, there’s a slight risk of identification.

Secure Connections for Business Networks
Businesses looking to establish secure remote connections to their local networks can rely on SOCKS5 proxies. When combined with proper authentication and encryption measures, these proxies ensure that remote connections remain secure and private.
The Power of Web Scraping
In today’s data-driven business landscape, web scraping has become an essential practice for extracting valuable insights from the vast amounts of unstructured data generated daily. SOCKS5 proxies offer a significant advantage for web scraping projects, allowing data extraction from any TCP or UDP transport, including sources like live video streams that HTTPS proxies cannot access.
Industry Applications of Web Scraping:
- Competitive Price Analysis: Maintain a competitive edge by using web scraping to keep track of industry pricing, aiding in the formulation of effective pricing strategies.
- Market Research: Gain insights into customer preferences and trends by scraping data on product feedback, driving informed product development and ensuring market demand.
- Enhanced Customer Service: Utilize web scraping to monitor brand mentions across social media, blogs, and forums, enabling prompt responses to customer inquiries and concerns, thereby fostering goodwill and enhancing public perception.
Configuring a SOCKS5 Proxy
To utilize a SOCKS5 proxy in your browser, you’ll need the proxy IP and port number provided by your proxy service. Here’s how to set it up on Chrome and Firefox:
For Chrome:
- Open the Settings via the dropdown menu in the upper right corner.
- Navigate to the bottom and select “Advanced”.
- Click on “System” and then “Open Proxy Settings”.
- In the proxy settings, tick the “SOCKS Proxy” checkbox.
- Input your SOCKS5 proxy IP and port in the designated field.
- Confirm with “Okay” and apply the changes in the main network settings.
For Firefox:
- Go to Preferences from the dropdown menu in the upper right corner.
- Scroll to “Network Proxy Settings” and select “Settings”.
- In the connection settings, choose “Manual Proxy Configuration”.
- Enter your proxy IP and port in the “SOCKS Host” field.
- Finalize with “Okay” to apply the new proxy settings.
Types of Proxies
Proxies are versatile tools that come in various types, each with unique characteristics and suited for different use cases. Here’s a simplified breakdown of the different kinds of SOCKS5 proxies:
Data Center Proxies: These proxies are housed in data centers and are known for their high speed, making them ideal for gaming or streaming. However, they can be easily identified as non-residential IPs, which might lead to blocks if detected during activities like web scraping.
Rotating Proxies: Rotating proxies change the IP address with each request, providing a higher level of anonymity. This is especially useful for web scraping, as it prevents detection by websites that may otherwise ban static IP addresses for bot-like activities.
Shared vs. Private Proxies:
- Shared Proxies: These are cost-effective and shared among multiple users. While they are more affordable, they may suffer from slower performance and security risks due to the shared nature.
- Private Proxies: Also known as dedicated proxies, they are used exclusively by one user, offering the highest security and performance levels without the risk of being affected by other users’ activities.
- Semi-Dedicated Proxies: A middle ground between shared and private, these proxies are shared with only a few users, providing a balance of security, speed, and cost.
Each type of proxy has its advantages and is suitable for different scenarios, from individual privacy needs to corporate data scraping operations. Choose the one that aligns best with your specific requirements and use case.
Conclusion: Why SOCKS5 Proxies Are the Smart Choice
In the digital age where data security and online privacy are paramount, SOCKS5 proxies emerge as the smart choice for individuals and businesses alike. With their ability to support multiple protocols, robust authentication methods, and dynamic port forwarding, SOCKS5 proxies offer a versatile and secure solution for a wide range of online activities. Whether it’s for bypassing geo-restrictions, enhancing performance, or maintaining a balance between anonymity and speed, SOCKS5 proxies provide the flexibility and efficiency required in today’s fast-paced online environment.
For those seeking to delve deeper into the world of proxies and unlock their full potential, twistory is your go-to resource. Stay informed and ahead of the curve by turning to twistory for comprehensive insights and valuable information on leveraging SOCKS5 proxies to your advantage.