In the digital lexicon, “proxy” can mean many things. Tools like Virtual Private Networks (VPNs) and Tor embody this term, offering a veil of anonymity for online browsing. But proxies aren’t just about privacy; they’re pivotal for websites to efficiently manage the swarm of web traffic via reverse proxies. This multifaceted nature of proxies often leads to puzzlement.
In the forthcoming article, we’ll untangle the complexities surrounding proxies. Prepare to dive into the essence of a proxy server, uncover the spectrum of proxy types, decipher their operations, and discover how they can be harnessed to enhance your online experience.
What is proxy server?
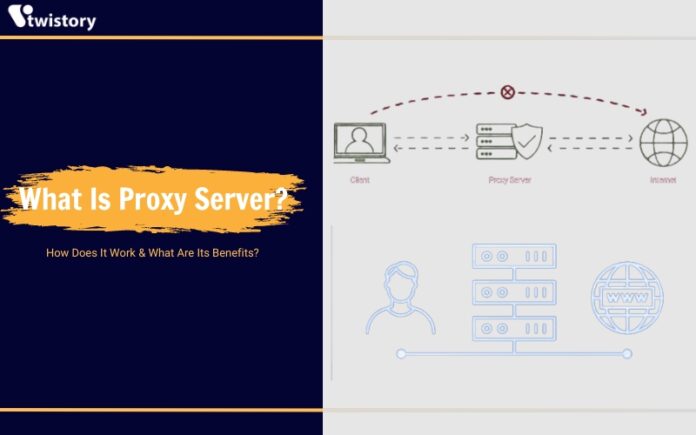
A proxy server stands as an intermediary between your internet activity and the vast expanse of the internet. It’s a mediator that separates the users from the web pages they visit. Depending on what you require, whether it’s for a specific task, security measures, or adhering to organizational guidelines, proxy servers offer a wide array of functionalities, safeguarding measures, and confidentiality levels.
When you navigate the internet through a proxy server, your online requests are sent through this mediator to the destination website. Typically, responses follow the same path back, passing through the proxy server before reaching you, though there are some exceptions to this process.
So, why use a proxy server at all? Why not just connect directly to websites? Proxy servers are not just about relaying information; they enhance security and improve network efficiency. They serve as a protective barrier and a filter for web content, manage shared network resources, and store (cache) data locally to expedite frequent requests. An effective proxy server not only secures users and the internal network from various online threats but also offers a significant degree of anonymity, thereby elevating your internet privacy.
How a proxy server works
Proxy servers function as intermediaries that connect you to the website you want to visit. When you make a request on the internet, the proxy server steps in to carry out this request on your behalf and deliver the result back to you.
This basic function holds true across various types of proxies. Standard proxies don’t envelop your data in encryption—they simply act on your instructions to retrieve web content. Yet, certain advanced proxies offer encryption services, effectively protecting your privacy from your internet service provider (ISP), though this also means the proxy server’s operator could access your data, requiring a high level of trust in the provider.
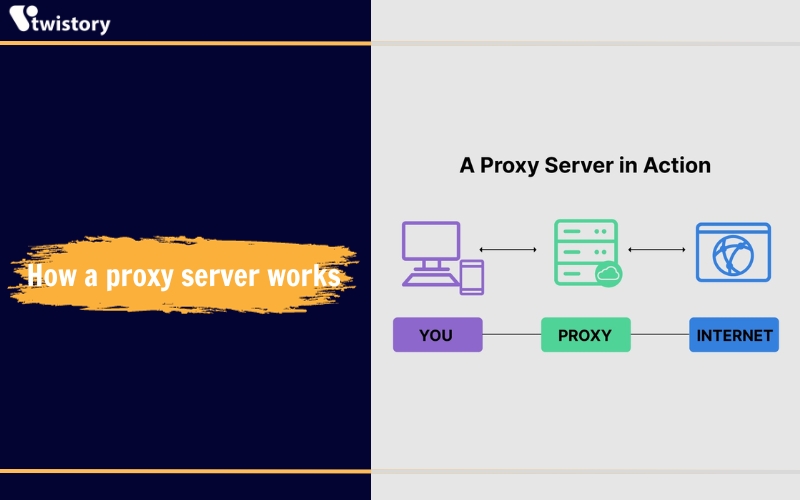
Additionally, proxies mask your IP address, making it appear as if you are accessing the web from a different location, thus protecting your privacy. However, be cautious, as non-encrypted proxies might inadvertently expose your real IP address.
Proxies can also serve as tools for internet filtering. In a corporate setting, a proxy server can enforce security protocols by regulating website access, allowing or blocking content based on the company’s preferences through the proxy’s IP address settings.
Types of proxies
There are various types of proxy servers, each designed for specific purposes. Here’s a rundown of some of the most prevalent ones.
Transparent HTTP proxies
Transparent HTTP proxies operate using the most basic proxy technology. They do not offer data encryption, unlike VPNs or SSH SOCKS proxies. Essentially, these proxies simply relay requests to the target servers.
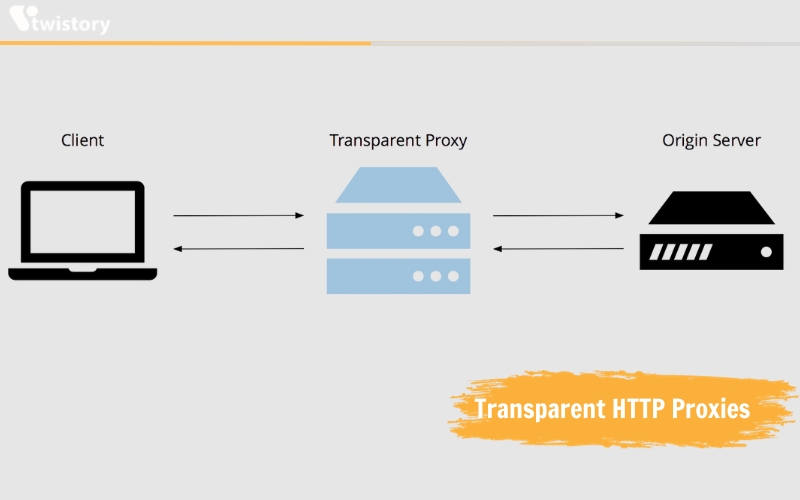
These proxies do not provide encryption or additional security measures to the connection, nor do they conceal the user’s IP address. They function by utilizing the standard X-Forwarded-For HTTP header.
For those seeking to safeguard their privacy or circumvent censorship, transparent proxies may not be the ideal option.
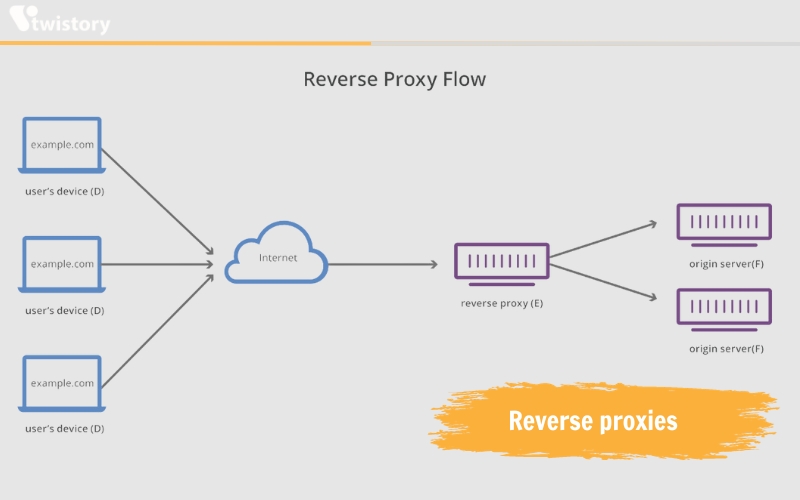
Reverse proxies
Reverse proxies are built on the technology underlying transparent proxying. Rather than handling connections for clients, reverse proxies receive connections on behalf of a server.
Reverse proxies are typically not relevant for individual users unless they are managing their own websites or are using a web application that utilizes a reverse proxy. However, they are a staple in the infrastructure of most large websites. Encountering a “504 Gateway Timeout” error is often an indication from the reverse proxy that it cannot retrieve a response from the backend server.
SOCKS Proxies
SOCKS, standing for Socket Secure, is a type of proxy technology that encrypts data. When you route your web traffic through a SOCKS proxy, the data is encrypted en route to the proxy server.
SOCKS proxies are similar to VPNs among the various types of proxies, though they are typically configured on a per-application basis rather than for the entire system.
The Secure Shell (SSH) protocol is commonly utilized for remote server access. In addition, it can also be used to the establishment of a SOCKS proxy through a remote server. This method will be explored in more depth later in the text.
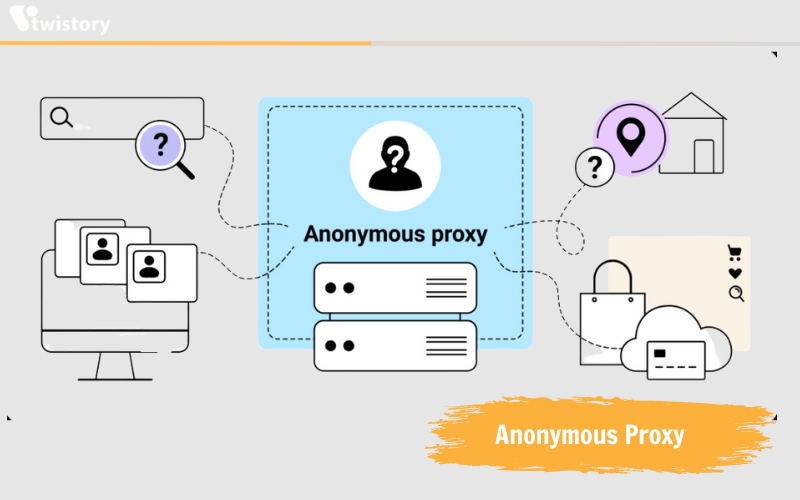
Anonymous Proxy
An anonymous proxy identifies its proxy status to websites but does not disclose your IP address, aiding in protecting your identity and maintaining the privacy of your online activities. Anonymous proxies can also prevent websites from delivering location-based targeted advertising. For example, if CNN.com identifies your location as Raleigh, NC, you would typically receive news relevant to that area. Anonymous browsing can hinder some forms of ad targeting, although it does not offer absolute anonymity.
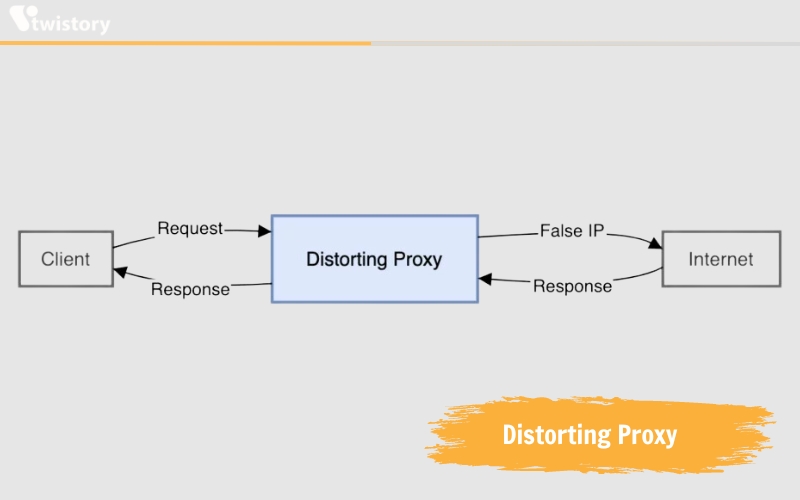
Distorting proxy
A distorting proxy server provides a false IP address on your behalf and acknowledges its role as a proxy. This type of proxy shares common goals with an anonymous proxy, but by relaying an incorrect IP, it enables you to appear as if you are accessing the internet from a different location. This is achieved by intercepting your web traffic and replacing your real IP address with a false one. By masking your true IP address, distorting proxy servers prevent websites from tracking your online activities and identifying your actual location.
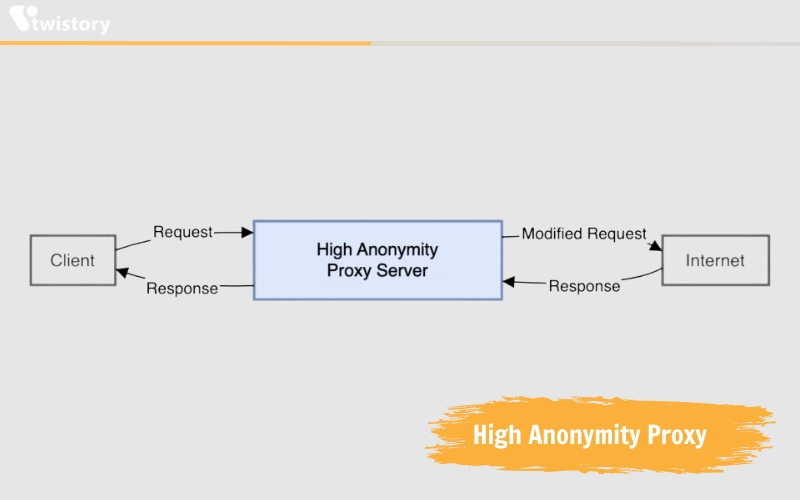
High Anonymity proxy
High anonymity proxy servers change the IP address they show to web servers at regular intervals, greatly complicating the task of matching online activities with their users.
Proxies offering high anonymity, such as those in the TOR Network, work by routing your internet traffic through a network of relay servers. This makes it very difficult for websites or third parties to track your online activities by linking them to your real IP address.
Why should you use a Proxy Server?
There are multiple incentives for using a proxy server, both for organizations and individuals.
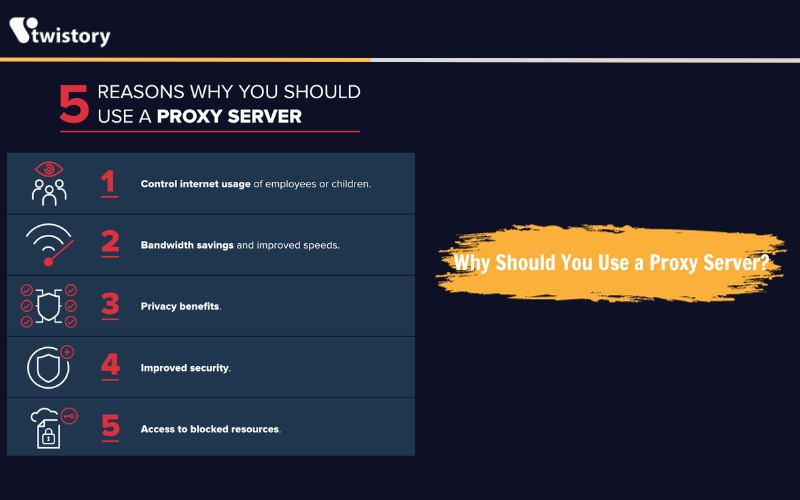
- Managing internet access: Companies and parents use proxies to direct and scrutinize how their employees or children utilize the internet. They can block access to certain sites and keep logs of internet usage, which helps in preventing non-work-related browsing during office hours.
- Saving bandwidth and enhancing speed: A good proxy server can improve network performance by caching frequently visited websites. This means less bandwidth usage and faster access for everyone when many people visit the same site.
- Ensuring privacy: Proxy servers are also used for more anonymous browsing. They can alter the IP address and other identifying information, making it difficult for the destination server to identify the original requester, thus preserving privacy.
- Boosting security: Beyond privacy, proxies can also offer additional security features. They can encrypt web requests, block access to malicious sites, and integrate with VPNs for secure remote access to the company network, protecting both company data and user privacy.
- Overcoming restrictions: Proxies can bypass geo-restrictions and content blocks, allowing users to access a wider range of content regardless of regional restrictions or company and government censorship.
Are proxy servers safe?
Proxy servers come with their own set of risks. Like VPNs, disreputable proxies may hijack your data for profit. It’s impossible to guarantee complete privacy with any third-party proxy. Nonetheless, a paid proxy service generally offers assurances against logging your activities.
Managing your own proxy server eliminates the risk of third-party mishandling, but it also means you’re responsible for its upkeep and defense. An improperly secured proxy could be exploited by unauthorized users, potentially leading to serious legal issues, so robust authentication is crucial.
One limitation of proxy servers is that they require application-specific configuration. This means that you must manually configure each application that you want to use the proxy with. If you do not configure an application correctly, your traffic may not be routed through the proxy, leaving it exposed. For more comprehensive privacy, you might consider using a VPN or the Tor network, as they cover all internet activity from your device.
Conclusion
In summary, proxy servers play a pivotal role in digital navigation, acting as a gateway that balances the need for security with the desire for unobstructed internet access. Through its own mechanisms, it enhances user privacy, strengthens network efficiency, and enforces content restrictions, all while adeptly handling complex internet protocols.
The detailed information provided by Twistory.net aims to clarify the multifaceted roles and benefits of proxy servers, highlighting their importance in both organizational and personal contexts. In addition to the information already provided, it is also worth mentioning that proxy servers can play a significant role in protecting user privacy by masking a user’s IP address and other identifying information. This can help to prevent online tracking and surveillance, and can also be useful for accessing geo-restricted content.